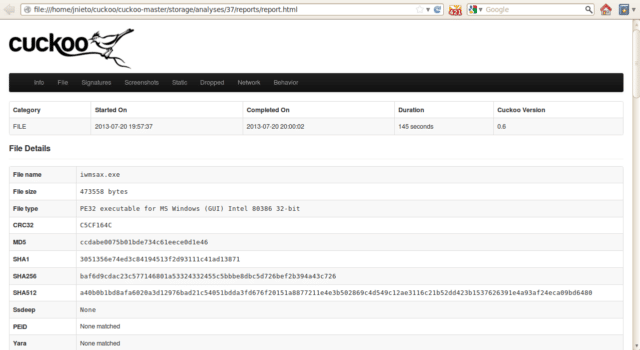
Cuckoo Sandbox is Open Source software for automating analysis of suspicious files. To do so it makes use of custom components that monitor the behaviour of the malicious processes while running in an isolated environment.
In other words, you can throw any suspicious file at it and in a matter of seconds Cuckoo will provide you back some detailed results outlining what such file did when executed inside an isolated environment.
Malware is the swiss-army knife of cybercriminals and any other adversary to your corporation or organization.
In these evolving times, detecting and removing malware artifacts is not enough: it’s vitally important to understand how they operate in order to understand the context, the motivations and the goals of a breach, for better protecting in the future.
Features
So what can it do? Cuckoo Sandbox is an advanced, extremely modular, and 100% open malware analysis system with infinite application opportunities.
By default it is able to:
- Analyze many different malicious files (executables, document expoits, Java applets) as well as malicious websites, in Windows, OS X, Linux, and Android virtualized environments.
- Trace API calls and general behavior of the file.
- Dump and analyze network traffic, even when encrypted.
- Perform advanced memory analysis of the infected virtualized system with integrated support for Volatility.
Even more interestingly, thanks to Cuckoo’s extensive modular design, you are able to customize both the processing and the reporting stages. Cuckoo provides you all the requirements to easily integrate the sandbox into your existing frameworks and storages with the data you want, in the way you want, with the format you want.
Use Cases
Use Cases
Cuckoo is designed to be used both as a standalone application as well as to be integrated in larger frameworks, thanks to its extremely modular design.
It can be used to analyze:
- Generic Windows executables
- DLL files
- PDF documents
- Microsoft Office documents
- URLs and HTML files
- PHP scripts
- CPL files
- Visual Basic (VB) scripts
- ZIP files
- Java JAR
- Python files
- Almost anything else
Thanks to its modularity and powerful scripting capabilities, there’s no limit to what you can achieve with Cuckoo.
You can download Cuckoo straight from Github:
|
1 |
git clone git://github.com/cuckoosandbox/cuckoo.git |
Or read more here.
