Powershell-RAT is a Python-based Gmail exfiltration RAT that can be used a Windows backdoor to send screenshots or other data as an e-mail attachment.
This RAT will help you during red team engagements to backdoor any Windows machines. It tracks the user activity using screen capture and sends the information to an attacker as an e-mail attachment.
It claims to not need Administrator access and is not currently detected by Anti-virus software.
How to setup Powershell-RAT Gmail Exfiltration RAT
- You need a throwaway Gmail email address
- Then enable “Allow less secure apps” by going to https://myaccount.google.com/lesssecureapps
- Modify the
$username&$passwordvariable for your account in theMail.ps1Powershell file - Modify
$msg.From&$msg.To.Addwith the throwaway Gmail address
How I do use Powershell-RAT Gmail Backdoor?
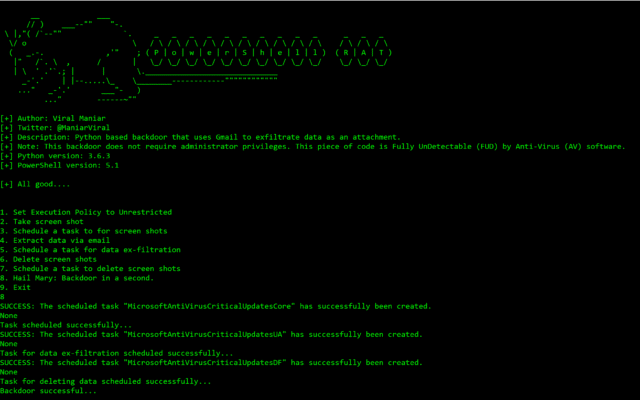
- Press 1: This option sets the execution policy to unrestricted using
Set-ExecutionPolicyUnrestricted. This is useful on administrator machine - Press 2: This takes the screenshot of the current screen on the user machine using
Shoot.ps1Powershell script - Press 3: This option backdoors the user machine using
schtasksand sets the task name toMicrosoftAntiVirusCriticalUpdatesCore - Press 4: This option sends an email from the user machine using
Powershell. These usesMail.ps1file to send screenshot as attachment to exfiltrate data - Press 5: This option backdoors the user machine using
schtasksand sets the task name toMicrosoftAntiVirusCriticalUpdatesUA - Press 6: This option deletes the screenshots from user machine to remain stealthy
- Press 7: This option backdoors the user machine using
schtasksand sets the task name toMicrosoftAntiVirusCriticalUpdatesDF - Press 8: This option performs all of the above with a single button
press 8on a keyboard. Attacker will receive an email every 5 minutes with screenshots as an email attachment. Screenshots will be deleted after 12 minutes - Press 9: Exit gracefully from the program or press
Control+C
Some other related tools are:
– PyExfil – Python Data Exfiltration Tools
– DET – Data Exfiltration Toolkit
– dnsteal – DNS Exfiltration Tool
And using Gmail as a backchannel there is:
– Gdog – Python Windows Backdoor With Gmail Command & Control
– Gcat – Python Backdoor Using Gmail For Command & Control
You can download Powershell-RAT here:
Or read more here.

exif says
Is this really a RAT or backdoor? I cannot see any remote connectivity.
Darknet says
Yah I think exfiltration backdoor is a more accurate title, calling it a RAT is pushing it a bit.