Sodium is a new, easy-to-use software library for encryption, decryption, signatures, password hashing and more. It is a portable, cross-compilable, installable, packageable fork of NaCl, with a compatible API, and an extended API to improve usability even further. Its goal is to provide all of the core operations needed to build higher-level cryptographic tools. Sodium […]
Archives for March 2018
XSStrike – Advanced XSS Fuzzer & Exploitation Suite
XSStrike is an advanced XSS detection suite, which contains a powerful XSS fuzzer and provides zero false positive results using fuzzy matching. XSStrike is the first XSS scanner to generate its own payloads. It is also built in an intelligent enough manner to detect and break out of various contexts. Features of XSStrike XSS Fuzzer […]
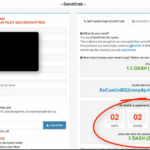
Bitdefender Releases FREE GandCrab Ransomware Decryption Tool
The latest ransomware kicking everyone’s ass is Gandcrab which has infected an estimated 50,000 computers, fortunately for the victims, Bitdefender has released a free Gandcrab ransomware decryption tool as a part of the No More Ransom Project. There’s nothing particularly notable about the ransomware itself other than it combines two existing exploit kits to compromise […]