One of the biggest stories of the year so far has been the scandal surrounding Cambridge Analytica that came out after a Channel 4 expose that demonstrated the depths they are willing to go to profile voters, manipulate elections and much more. It’s kicking off in the UK and the US and Mark Zuckerberg has […]
Archives for March 2018
GetAltName – Discover Sub-Domains From SSL Certificates
GetAltName it’s a little script to discover sub-domains that can extract Subject Alt Names for SSL Certificates directly from HTTPS websites which can provide you with DNS names or virtual servers. It’s useful in a discovery phase of a pen-testing assessment, this tool can provide you with more information about your target and scope. Features […]
Memcrashed – Memcached DDoS Exploit Tool
Memcrashed is a Memcached DDoS exploit tool written in Python that allows you to send forged UDP packets to a list of Memcached servers obtained from Shodan. This is related to the recent record-breaking Memcached DDoS attacks that are likely to plague 2018 with over 100,000 vulnerable Memcached servers showing up in Shodan. What is […]
QualysGuard – Vulnerability Management Tool
QualysGuard is a web-based vulnerability management tool provided by Qualys, Inc, which was the first company to deliver vulnerability management services as a SaaS-based web-service. From reviews, it seems like a competent tool with a low rate of false positives that is fairly easy to work with and keep the more ‘dangerous’ parts of vulnerability […]
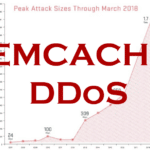
Memcached DDoS Attacks Will Be BIG In 2018
So after the massive DDoS attack trend in 2016 it seems like 2018 is going to the year of the Memcached DDoS amplification attack with so many insecure Memcached servers available on the public Internet. Unfortunately, it looks like a problem that won’t easily go away as there are so many publically exposed, poorly configured […]