Fern Wifi Cracker is a Wireless security auditing and attack software program written using the Python Programming Language and the Python Qt GUI library, the program is able to crack and recover WEP/WPA/WPS keys and also run other network based attacks on wireless or ethernet based networks.
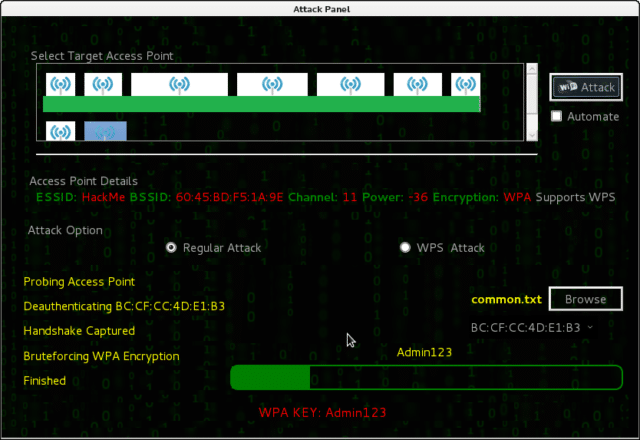
The Software runs on any Linux machine with prerequisites installed, and it has been tested on Ubuntu KDE/Gnome, BackTrack Linux and BackBox Linux.
What is a Wifi Cracker
A Wifi Cracker is a tool or piece of software designed to help with the recovery of Wireless Access Point (WAP) keys from WPA2 or WPS secured networks.
There are various Wifi Cracker tools available such as:
– Infernal Twin – Automated Wireless Hacking Suite
– FruityWifi – Wireless Network Auditing Tool
– wifite – Mass Wifi WEP/WPA Key Cracking Tool
– Kismet – Wireless Network Hacking, Sniffing & Monitoring
Features of Fern Wifi Cracker
Fern currently supports:
- WEP Cracking with Fragmentation,Chop-Chop, Caffe-Latte, Hirte, ARP Request Replay or WPS attack
- WPA/WPA2 Cracking with Dictionary or WPS based attacks
- Automatic saving of key in database on successful crack
- Automatic Access Point Attack System
- Session Hijacking (Passive and Ethernet Modes)
- Access Point MAC Address Geo Location Tracking
- Internal MITM Engine
- Bruteforce Attacks (HTTP,HTTPS,TELNET,FTP)
- Update Support
Prerequisites for Fern Wifi Cracker
Fern requires the following to run properly:
- Aircrack-NG
- Python-Scapy
- Python Qt4
- Python
- Subversion
- Xterm
- Reaver (for WPS Attacks)
- Macchanger
You can download Fern Wireless Cracker here:
Or read more here.

Henry says
Hello,
I wasn’t sure how to go about asking so figured id just ask on one of your recent posts.
I’m curious about types of malware. It is possible to combined the attributes of reverse shell malware and also the replicating attributes of a worm?
So basically the malware would propagate round a LAN and give the attacker access to every machine it infects.
I understand you would have to be an expert to code something like this. However, is it possible?
Henry :)
Darknet says
Yes it’s possible, and such things already exist. Most worms work via an exploit to gain access, then scan the network and spread further.