HashData is a Ruby-based command-line REPL Hash Identifying Tool with support for a lot of different (most popular) hash types.
Installation
|
1 |
$ gem install hashdata |
Usage
Command Line
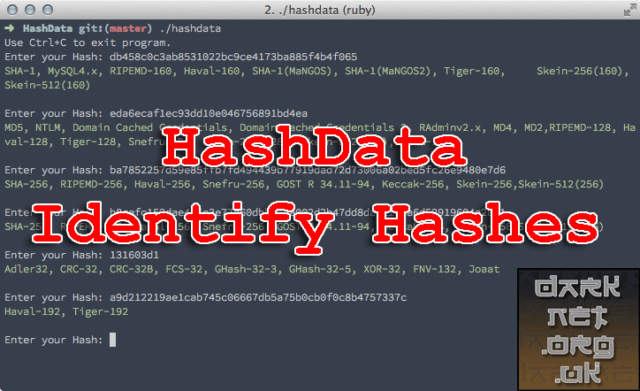
When installed, run hashdata and paste in hashes when prompted.
Library
Example Script:
|
1 2 3 |
require 'hashdata' hash = HashData.new puts(hash.check_type("1111111111111",'DES')) |
The above should output true. The library only matches the start of your second input, this means that you can check something is an MD5 hash without having to worry about if it is from Joomla or Unix for example.
Hashes Supported
- Adler32
- Blowfish(Eggdrop), Blowfish(OpenBSD)
- CRC-16, CRC-16-CCITT
- CRC-32, CRC-32B
- CRC-96(ZIP)
- Domain Cached Credentials, Domain Cached Credentials 2
- DES(Unix), DES(Oracle)
- FCS-16, FCS-32
- FNV-132, FNV-164
- GOST R 34.11-94
- GHash-32-3, GHash-32-5
- Haval-128, Haval-160, Haval-192, Haval-224, Haval-256
- Joaat
- Lineage II C4
- LM
- Lotus Domino
- MD2, MD4, MD5
- MD5(Joomla), MD5(osCommerce), MD5(PalshopCMS)
- MD5(APR), MD5(Cisco PIX), MD5(Unix)
- MD5(IP.Board), MD5(MyBB), MD5(phpBB3), MD5(WordPress)
- MySQL3.x, MySQL4.x, MySQL5.x
- MSSQL(2000), MSSQL(2005), MSSQL(2008)
- NTLM
- RAdmin v2.x
- RIPEMD-128, RIPEMD-160, RIPEMD-256, RIPEMD-320
- SAM(LM_Hash:NT_Hash)
- SHA-1, SHA-1(Django), SHA-1(MaNGOS), SHA-1(MaNGOS2)
- SHA-224
- SHA-256, SHA-256(Django), SHA-256(Unix)
- SHA3-224, SHA3-256, SHA3-384, SHA3-512
- SHA-384, SHA-384(Django)
- SHA-512, SHA-512(Drupal), SHA-512(Unix)
- SSHA-1
- Skein-256, Skein-256(128), Skein-256(160), Skein-256(224)
- Skein-512, Skein-512(128), Skein-512(160), Skein-512(224), Skein-512(256), Skein-512(384)
- Skein-1024, Skein-1024(384), Skein-1024(512)
- Snefru-128, Snefru-256
- Tiger-128, Tiger-160, Tiger-192
- VNC
- Whirlpool
- XOR-32
You can download HashData here:
Or read more here.

Volker says
You do not need a full dev environment to identify hashes. I simply wrapped the available data into a one-page JavaScript application: https://www.wyae.de/docs/hashid/