The debate surrounding encryption backdoors has been raging on for years with governments (that typically don’t really understand the things they are pushing for) requesting all software have government ‘secured’ backdoor keys. This is now getting more serious in Europe with the EC actually forcing the issue (in a passive aggressive kind of way for […]
Archives for March 2017
HashPump – Exploit Hash Length Extension Attack
HashPump is a C++ based command line tool to exploit the Hash Length Extension Attack with various hash types supported, including MD4, MD5, SHA1, SHA256, and SHA512. There’s a good write-up of how to use this in practical terms here: Plaid CTF 2014: mtpox Usage
|
1 2 3 4 5 6 7 8 9 10 11 |
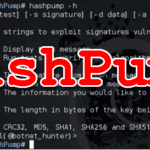
$ hashpump -h HashPump [-h help] [-t test] [-s signature] [-d data] [-a additional] [-k keylength] HashPump generates strings to exploit signatures vulnerable to the Hash Length Extension Attack. -h --help Display this message. -t --test Run tests to verify each algorithm is operating properly. -s --signature The signature from known message. -d --data The data from the known message. -a --additional The information you would like to add to the known message. -k --keylength The length in bytes of the key being used to sign the original message with. Version 1.2.0 with CRC32, MD5, SHA1, SHA256 and SHA512 support. <Developed by bwall(@botnet_hunter)> |
You can download HashPump here:
|
1 2 3 4 5 |
$ git clone https://github.com/bwall/HashPump.git $ apt-get install g++ libssl-dev $ cd HashPump $ make $ make install |
Or read more […]
Kadimus – LFI Scanner & Exploitation Tool
Kadimus is an LFI scanner and exploitation tool for Local File Inclusion vulnerability detection and intrusion. Installation
|
1 2 |
$git clone https://github.com/P0cL4bs/Kadimus.git $ cd Kadimus |
Then you can run the configure file:
|
1 |
./configure |
Then:
|
1 |
$ make |
Features Check all url parameters /var/log/auth.log RCE /proc/self/environ RCE php://input RCE data://text RCE Source code disclosure Multi thread scanner Command shell interface through HTTP Request Proxy support […]
LastPass Hacked – Leaking Passwords Via Chrome Extension
LastPass Hacked – Leaking Passwords is not new, last week its Firefox extension was picked apart – now this week it’s Chrome extension is giving up its goodies. I’ve always found LastPass a bit suspect, even though they are super easy to use, and have a nice UI they’ve had TOO many serious security issues […]
SessionGopher – Session Extraction Tool
SessionGopher is a PowerShell Session Extraction tool that uses WMI to extract saved session information for remote access tools such as WinSCP, PuTTY, SuperPuTTY, FileZilla, and Microsoft Remote Desktop. The tool can find and decrypt saved session information for remote access tools. It has WMI functionality built in so it can be run remotely, its […]