HashPump is a C++ based command line tool to exploit the Hash Length Extension Attack with various hash types supported, including MD4, MD5, SHA1, SHA256, and SHA512.
There’s a good write-up of how to use this in practical terms here: Plaid CTF 2014: mtpox
Usage
|
1 2 3 4 5 6 7 8 9 10 11 |
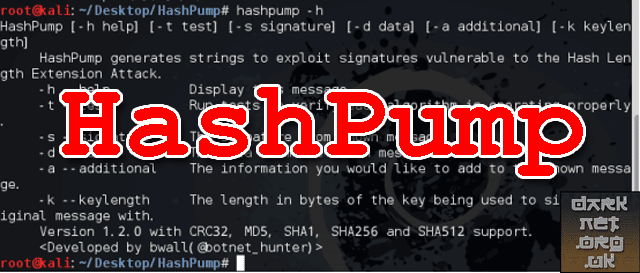
$ hashpump -h HashPump [-h help] [-t test] [-s signature] [-d data] [-a additional] [-k keylength] HashPump generates strings to exploit signatures vulnerable to the Hash Length Extension Attack. -h --help Display this message. -t --test Run tests to verify each algorithm is operating properly. -s --signature The signature from known message. -d --data The data from the known message. -a --additional The information you would like to add to the known message. -k --keylength The length in bytes of the key being used to sign the original message with. Version 1.2.0 with CRC32, MD5, SHA1, SHA256 and SHA512 support. <Developed by bwall(@botnet_hunter)> |
You can download HashPump here:
|
1 2 3 4 5 |
$ git clone https://github.com/bwall/HashPump.git $ apt-get install g++ libssl-dev $ cd HashPump $ make $ make install |
Or read more here.
