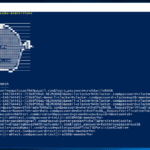
mimikittenz is a post-exploitation powershell tool that utilizes the Windows function ReadProcessMemory() in order to extract plain-text passwords from various target processes. The aim of mimikittenz is to provide user-level (non-admin privileged) sensitive data extraction in order to maximise post exploitation efforts and increase value of information gathered per target. NOTE: This tool is targeting […]
Archives for September 2016
Massive Yahoo Hack – 500 Million Accounts Compromised
So if you are a Yahoo user (which most of us probably have been at some point) you will be aware of the Yahoo Hack – with 200 Million e-mail addresses being up for sale on the black market it seems up to 500 million have been compromised in one of the biggest hacks yet. […]
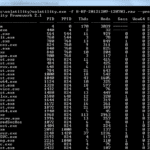
Volatility Framework – Advanced Memory Forensics Framework
The Volatility Framework is an an advanced, completely open collection of tools for memory forensics, implemented in Python under the GNU General Public License, for the extraction of digital artifacts from volatile memory (RAM) samples. The extraction techniques are performed completely independent of the system being investigated but offer visibility into the runtime state of […]
OWASP OWTF – Offensive Web Testing Framework
OWASP Offensive Web Testing Framework is a project focused on penetration testing efficiency and alignment of security tests to security standards like: The OWASP Testing Guide (v3 and v4), the OWASP Top 10, PTES and NIST. The purpose of this tool is to automate the manual and uncreative parts of pen testing. For example, Figuring […]
Tesla Hack – Remote Access Whilst Parked or Driving
The big buzz on my Twitter this week was about the Tesla Hack carried out by a Chinese crew called Keen Security Lab. It’s no big surprise even though Tesla is known for being fairly security concious and proactive about it. With it being a connected car, that’s pretty important that any remote control capabilities […]