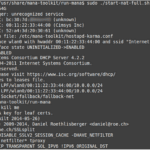
MANA Toolkit is a set of tools for rogue access point (evilAP) attacks and wireless MiTM. More specifically, it contains the improvements to KARMA attacks implemented into hostapd, as well as some useful configs for conducting MitM once you’ve managed to get a victim to connect. Contents MANA Toolkit contains: kali/ubuntu-install.sh – simple installers for […]
Archives for September 2016
BBQSQL – Blind SQL Injection Framework
BBQSQL is a blind SQL injection framework written in Python. It is extremely useful when attacking tricky SQL injection vulnerabilities. BBQSQL is also a semi-automatic tool, allowing quite a bit of customization for those hard to trigger SQL injection findings. The tool is built to be database agnostic and is extremely versatile. It also has […]
Two Israeli Men Arrested For Running VDoS-s.com DDoS Service
DDoS or Booter services have been around for a while, but VDoS-s.com was a particularly slick (and shameless) one with a content marketing strategy and active social media accounts. Two Israeli men were arrested for running the service after ironically being hacked by a security researcher. They called their service a ‘Stresser’ and claimed to […]
PunkSPIDER – A Web Vulnerability Search Engine
PunkSPIDER is a global-reaching web vulnerability search engine aimed at web applications. The goal is to allow the user to determine vulnerabilities in websites across the Internet quickly, easily, and intuitively. Please use PunkSPIDER responsibly. In simple terms, that means the authors have created a security scanner and the required architecture that can execute a […]
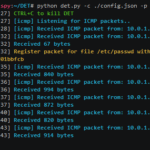
DET – Data Exfiltration Toolkit
DET is a proof of concept Data Exfiltration Toolkit using either single or multiple channel(s) at the same time. The idea behind DET was to create a generic tool-kit to plug any kind of protocol/service to test implemented Network Monitoring and Data Leakage Prevention (DLP) solutions configurations, against different data exfiltration techniques. Features DET already […]