Crypto ransomware is a type of malware that holds you ransom by encrypting your files and has been around for a while, but the FBI recently said at a cyber security summit that they advise companies that fall victim just to pay.
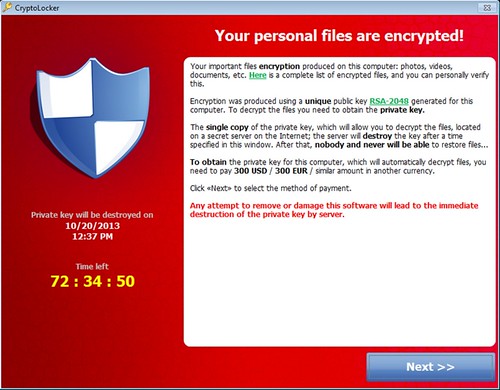
Such malware tends to use pretty strong encryption algorithms like RSA-2048, which you aren’t going to be able to crack. So yah, pragmatically speaking if you got stung by this type of infection – you don’t really have much choice other than to pay.
The Federal Bureau of Investigation (FBI) advises companies that fall victim to hacks involving Cryptolocker, Cryptowall or other forms of ransomware to pay the ransom, said Joseph Bonavolonta, an assistant special agent with FBI, speaking at the Cyber Security Summit 2015 in Boston
Noting that while the agency has their back, “the ransomware is that good,” the Security Ledger quoted Bonavolonta as saying. “To be honest, we often advise people just to pay the ransom” because efforts by the Bureau to defeat the encryption used have proved futile.
But he added that the success of the ransomware has benefited the victims in a twisted way because having so many people willing to pay has driven the price down since malware authors are less likely to try to charge excessive ransom amounts.
Even with all the power the Bureau has, they can’t crack this kind of stuff. And well even if they could, they aren’t going to fire up their super computer farm again some companies encrypted stash of ransomed Excel documents.
It’s interesting to see them kind of officially say it though, that this ransomware is really well made and you don’t really have much choice.
Stu Sjouwerman, CEO at KnowBe4, told SCMagazine.com that he agrees in part with the Bonavolonta’s advice because if a company stands to lose week’s or month’s worth of work while trying to decrypt its files, paying out $500 or so in ransom can be viewed as the equivalent of what he called a cheap “security audit.”
However, Sjouwerman said that the FBI should focus more on education and prevention rather than just giving in to the bad guys.
“I understand where they are coming from but rewarding the bad guys for bad behavior will only reinforce bad behavior,” Sjouwerman said.
He recommended that companies have backup files that are regularly tested, be religious about application and operating system updates, and ensure employees are trained in cybersecurity best practices.
So yah, if you run an organisation, without backups – you kinda deserve this kinda scam coming in your direction. But just be aware, if you do get an infection it could be costly and a royal pain in the arse.
Source: SC Magazine

sudon't says
If your files are held hostage, pay up. if your loved ones are held hostage, we might prosecute you if you pay up.