Ghost Phisher is a Wireless and Ethernet security auditing and phishing attack tool written using the Python Programming Language and the Python Qt GUI library, the program is able to emulate access points and deploy. The tool comes with a fake DNS server, fake DHCP server, fake HTTP server and also has an integrated area […]
Phishing
SPF (SpeedPhish Framework) – E-mail Phishing Toolkit
SPF (SpeedPhish Framework) is a an e-mail phishing toolkit written in Python designed to allow for quick recon and deployment of simple social engineering phishing exercises. There are also other popular Phishing tools are frameworks such as: – Phishing Frenzy – E-mail Phishing Framework – Gophish – Open-Source Phishing Framework – sptoolkit Rebirth – Simple […]
Phishing Frenzy – E-mail Phishing Framework
Phishing Frenzy is an Open Source Ruby on Rails e-mail phishing framework designed to help penetration testers manage multiple, complex phishing campaigns. The goal of the project is to streamline the phishing process while still providing clients the best realistic phishing campaign possible. This goal is obtainable through campaign management, template reuse, statistical generation, and […]
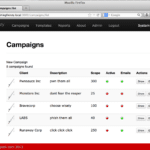
Gophish – Open-Source Phishing Framework
Gophish is a phishing framework that makes the simulation of real-world phishing attacks very straight forwards. The idea behind gophish is simple – make industry-grade phishing training available to everyone. There are various other similar tools available such as Simple Phishing Toolkit and sptoolkit Rebirth. I wonder if this is the beginning of an emergence […]
ICANN Hacked Including Root DNS Systems
So another hack has been exposed, this time on ICANN – which is pretty bad. They are the database of the Internet basically, including the root zone system which is the highest authority for DNS requests. “The Internet Corporation for Assigned Names and Numbers (ICANN) is a non-profit organization that is responsible for the coordination […]