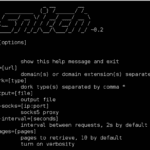
Snitch is an information gathering tool which automates the process for a specified domain. Using built-in dork categories, this tool helps gather specified information domains which can be found using web search engines. It can be quite useful in early phases of penetration tests (commonly called the Information Gathering phase). snitch can identify general information, […]
information gathering
DMitry – Deepmagic Information Gathering Tool
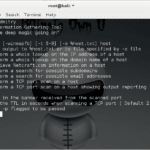
DMitry (Deepmagic Information Gathering Tool) is a UNIX/(GNU) Linux Command Line program coded purely in C with the ability to gather as much information as possible about a host. DMitry has a base functionality with the ability to add new functions, the basic functionality of DMitry allows for information to be gathered about a target […]
Automater – IP & URL OSINT Tool For Analysis
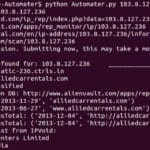
Automater is a URL/Domain, IP Address, and Md5 Hash OSINT tool aimed at making the analysis process easier for intrusion Analysts. Given a target (URL, IP, or HASH) or a file full of targets Automater will return relevant results from sources like the following: IPvoid.com, Robtex.com, Fortiguard.com, unshorten.me, Urlvoid.com, Labs.alienvault.com, ThreatExpert, VxVault, and VirusTotal. By […]
WAFW00F – Fingerprint & Identify Web Application Firewall (WAF) Products
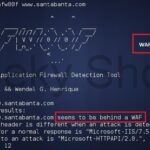
WAFW00F is a Python tool to help you fingerprint and identify Web Application Firewall (WAF) products. It is an active reconnaissance tool as it actually connects to the web server, but it starts out with a normal HTTP response and escalates as necessary. You can override or include your own headers, it has SOCKS and […]
Recon-ng – Web Reconnaissance Framework
Recon-ng is a full-featured Web Reconnaissance Framework written in Python. Complete with independent modules, database interaction, interactive help, and command completion – Recon-ng provides a powerful environment in which open source web-based reconnaissance can be conducted quickly and thoroughly. Recon-ng has a look and feel and even command flow similar to the Metasploit Framework, reducing […]