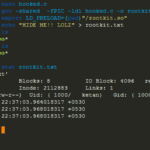
BEURK is an userland preload rootkit for GNU/Linux, heavily focused around anti-debugging and anti-detection. Being a userland rootkit it gives limited privileges (whatever the user has basically) vs a superuser or root level rootkit. Features Hide attacker files and directories Realtime log cleanup (on utmp/wtmp) Anti process and login detection Bypass unhide, lsof, ps, ldd, […]
rootkit
Android Malware Giving Phones a Hummer
So Android Malware has always been quite a problem, especially with it being so easy to install random .apk files and the proliferation of 3rd party app stores. Also so many people with rooted phones and the fact that software installed can root your phone and take complete control. The current worry is the Hummer […]
Azazel – Userland Anti-debugging & Anti-detection Rootkit
Azazel is a userland rootkit written in C based off of the original LD_PRELOAD technique from Jynx rootkit. It is more robust and has additional features, and focuses heavily around anti-debugging and anti-detection. Features include log cleaning, pcap subversion, and more. Features Anti-debugging Avoids unhide, lsof, ps, ldd detection Hides files and directories Hides remote […]
TDL AKA Alureon Rootkit Now Infecting 64-Bit Windows 7 Platform
As we’ve come to expect, the malware guys are always at the leading edge of technological development. Now there are rootkits infecting 64-Bit versions of Windows, which have been thought of as fairly safe by most parties. The rootkit in questions is a fairly well known variant (TDL/Alureon) and has been around for several years, […]
Nasty Trojan Zeus Evades Antivirus Software
This is one nasty piece of malware, seems like it’s working on a low level as per rootkits, there aren’t many technical details but it may well be operating on a Ring 0 level. The level of detection by AV software is quite scary, especially since the malware is specifically targeting bank login details and […]