The OWASP Amass Project is a DNS Enumeration, Attack Surface Mapping & External Asset Discovery tool to help information security professionals perform network mapping of attack surfaces and perform external asset discovery using open source information gathering and active reconnaissance techniques.
Information Gathering Techniques Used by OWASP Amass for DNS Enumeration and More
The main functionality of Amass is as follows:
- DNS: Basic enumeration, Brute forcing (optional), Reverse DNS sweeping, Subdomain name alterations/permutations, Zone transfers (optional)
- Scraping: Ask, Baidu, Bing, DNSDumpster, DNSTable, Dogpile, Exalead, Google, HackerOne, IPv4Info, Netcraft, PTRArchive, Riddler, SiteDossier, ViewDNS, Yahoo
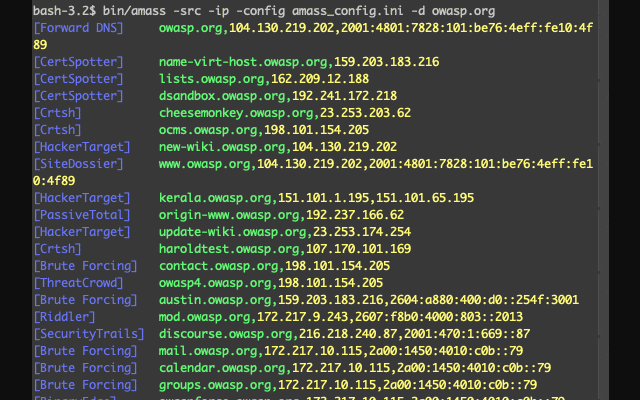
- Certificates: Active pulls (optional), Censys, CertSpotter, Crtsh, Entrust, GoogleCT
- APIs: AlienVault, BinaryEdge, BufferOver, CIRCL, CommonCrawl, DNSDB, GitHub, HackerTarget, IPToASN, Mnemonic, NetworksDB, PassiveTotal, Pastebin, RADb, Robtex, SecurityTrails, ShadowServer, Shodan, Spyse (CertDB & FindSubdomains), Sublist3rAPI, TeamCymru, ThreatCrowd, Twitter, Umbrella, URLScan, VirusTotal, WhoisXML
- Web Archives: ArchiveIt, ArchiveToday, Arquivo, LoCArchive, OpenUKArchive, UKGovArchive, Wayback
Usage of Amass for DNS Enumeration, Attack Surface Mapping & External Asset Discovery
The Amass tool has several subcommands shown below for handling your Internet exposure investigation.
- intel – Collect open-source intelligence for investigation of the target organization
- enum – Perform DNS enumeration and network mapping of systems exposed to the Internet
- viz – Generate visualizations of enumerations for exploratory analysis
- track – Compare results of enumerations against common target organizations
- db – Manage the graph databases storing the enumeration results
Each subcommand has its own arguments, for example, the ‘intel’ subcommand.
The intel subcommand can help you discover additional root domain names associated with the organization you are investigating. The data source sections of the configuration file are utilized by this subcommand in order to obtain passive intelligence, such as reverse whois information.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
-active Enable active recon methods -addr IPs and ranges (192.168.1.1-254) separated by commas -asn ASNs separated by commas (can be used multiple times) -cidr CIDRs separated by commas (can be used multiple times) -config Path to the INI configuration file -d Domain names separated by commas (can be used multiple times) -demo Censor output to make it suitable for demonstrations -df Path to a file providing root domain names -dir Path to the directory containing the graph database -ef Path to a file providing data sources to exclude -exclude Data source names separated by commas to be excluded -if Path to a file providing data sources to include -include Data source names separated by commas to be included -ip Show the IP addresses for discovered names -ipv4 Show the IPv4 addresses for discovered names -ipv6 Show the IPv6 addresses for discovered names -list Print the names of all available data sources -log Path to the log file where errors will be written -max-dns-queries Maximum number of concurrent DNS queries -noresolvrate Disable resolver rate monitoring -noresolvscore Disable resolver reliability scoring -o Path to the text output file -org Search string provided against AS description information -p Ports separated by commas (default: 443) -public-dns Use public-dns.info resolvers -r IP addresses of preferred DNS resolvers (can be used multiple times) -rf Path to a file providing preferred DNS resolvers -src Print data sources for the discovered names -timeout Number of minutes to execute the enumeration -whois All discovered domains are run through reverse whois |
It has some visualization capabilities and can also output to other tools and in various formats such as D3.js, GEXF, Graphistry JSON, VisJS and Maltego format.
You can download Amass here:
Linux: amass_v3.4.2_linux_amd64.zip
Windows: amass_v3.4.2_windows_amd64.zip
Source: Amass-v3.4.2.zip
Or read more here.
