zANTI is an Android Wireless Hacking Tool that functions as a mobile penetration testing toolkit that lets you assess the risk level of a network using your mobile device for free download. This easy to use mobile toolkit enables IT Security Administrators to simulate an advanced attacker to identify the malicious techniques they use in […]
Archives for 2020
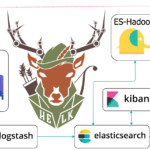
HELK – Open Source Threat Hunting Platform
The Hunting ELK or simply the HELK is an Open-Source Threat Hunting Platform with advanced analytics capabilities such as SQL declarative language, graphing, structured streaming, and even machine learning via Jupyter notebooks and Apache Spark over an ELK stack. This project was developed primarily for research, but due to its flexible design and core components, […]
Trape – OSINT Analysis Tool For People Tracking
Trape is an OSINT analysis tool, which allows people to track and execute intelligent social engineering attacks in real-time. It was created with the aim of teaching the world how large Internet companies could obtain confidential information. Example types of information are the status of sessions of their websites or services and control their users […]
Fuzzilli – JavaScript Engine Fuzzing Library
Fuzzilii is a JavaScript engine fuzzing library, it’s a coverage-guided fuzzer for dynamic language interpreters based on a custom intermediate language (“FuzzIL”) which can be mutated and translated to JavaScript. When fuzzing for core interpreter bugs, e.g. in JIT compilers, semantic correctness of generated programs becomes a concern. This is in contrast to most other […]
OWASP APICheck – HTTP API DevSecOps Toolset
APICheck is an HTTP API DevSecOps toolset, it integrates existing HTTP APIs tools, creates execution chains easily and is designed for integration with third-party tools in mind. APICheck is comprised of a set of tools that can be connected to each other to achieve different functionalities, depending on how they are connected. It allows you […]