BDFProxy allows you to patch binaries via MiTM with The Backdoor Factory combined with mitmproxy enabling on the fly patching of binary downloads (software updates for example) from vendors that don’t validate data integrity.
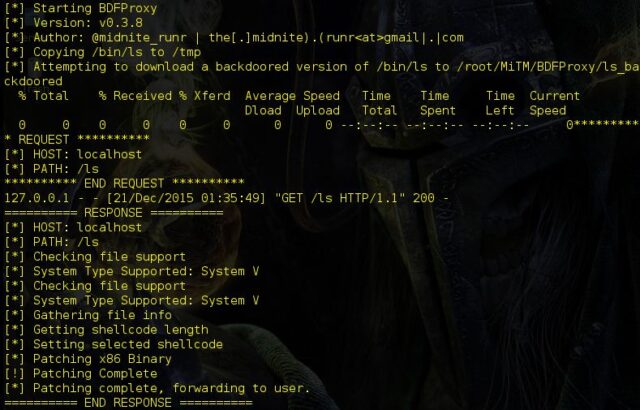
The Backdoor Factory allows you to patch binaries with shell-code so combining that with mitmproxy, which is a Python proxy-server that can catch HTTP, change traffic on the fly, replay traffic, decode and render primitive data types – gives you BDFProxy.
A lot of security tool websites still serve binaries via non-SSL/TLS means – plus imagine how many do it outside of the security space (e.g. sysinternals, malwarebytes, sourceforce, wireshark etc).
BDFProxy – Patch Binaries via MiTM – Installation and Requirements
Tested on all Kali Linux builds, whether a physically beefy laptop, a Raspberry Pi, or a VM, each can run BDFProxy.
Requires:
- Pefile – most recent
- ConfigObj
- mitmProxy – Kali Build .10
- BDF – most current
- Capstone (part of BDF)
To install on Kali:
|
1 2 |
apt-get update apt-get install bdfproxy |
Docker:
|
1 2 3 4 5 |
# sudo echo 1 > /proc/sys/net/ipv4/ip_forward # linux # sudo sysctl -w net.inet.ip.forwarding=1 # macOS docker pull secretsquirrel/bdfproxy docker run -it -p 8080:8080 secretsquirrel/bdfproxy bash # ./bdf_proxy.py |
Testing:
Suppose you want to use your browser with Firefox and FoxyProxy to connect to test your setup.
Update your config as follows:
|
1 |
transparentProxy = None |
Configure FoxyProxy to use BDFProxy as a proxy, default port in the config is 8080.
BDFProxy – Patch Binaries via MiTM – Logging
There is logging in BDFProxy, the proxy window will quickly fill with massive amounts of cat links depending on the client you are testing. Use tail -f proxy.log to see what is getting patched and blocked by your blacklist settings. However, keep an eye on the main proxy window if you have chosen to patch binaries manually, things move fast and behind the scenes there is multi-threading of traffic, but the initial requests and responses are locking for your viewing pleasure.
You can download BDFProxy here:
Or read more here.
