DNSRecon is a Python based DNS enumeration script designed to help you audit your DNS security and configuration as part of information gathering stage of a pen-test. DNS reconnaissance is an important step when mapping out domain resources, sub-domains, e-mail servers and so on and can often lead to you finding an old DNS entry pointing to an unmaintained, insecure server.
It’s also considered passive information gathering, as it’s a way to gather a map of company/target resources without alerting IDS/IPS systems by doing active probes/scans.
Features
DNSRecon provides the ability to perform:
- Check all NS Records for Zone Transfers
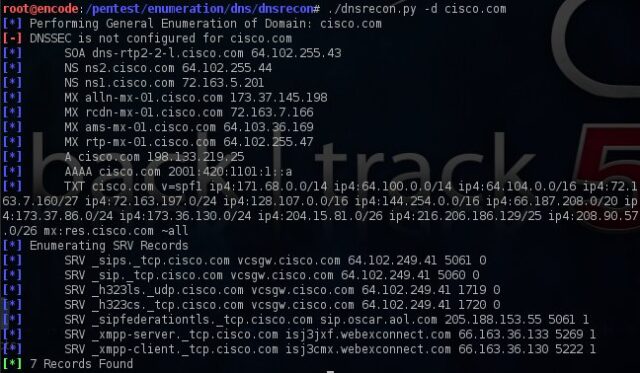
- Enumerate General DNS Records for a given Domain (MX, SOA, NS, A, AAAA, SPF and TXT)
- Perform common SRV Record Enumeration. Top Level Domain (TLD) Expansion
- Check for Wildcard Resolution
- Brute Force subdomain and host A and AAAA records given a domain and a wordlist
- Perform a PTR Record lookup for a given IP Range or CIDR
- Check a DNS Server Cached records for A, AAAA and CNAME Records provided a list of host records in a text file to check
- Enumerate Common mDNS records in the Local Network Enumerate Hosts and Subdomains using Google
Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 |
root@box:~# dnsrecon -h Usage: dnsrecon.py Options: -h, --help Show this help message and exit -d, --domain Domain to Target for enumeration. -r, --range IP Range for reverse look-up brute force in formats (first-last) or in (range/bitmask). -n, --name_server Domain server to use, if none is given the SOA of the target will be used -D, --dictionary Dictionary file of sub-domain and hostnames to use for brute force. -f Filter out of Brute Force Domain lookup records that resolve to the wildcard defined IP Address when saving records. -t, --type Specify the type of enumeration to perform: std To Enumerate general record types, enumerates. SOA, NS, A, AAAA, MX and SRV if AXRF on the NS Servers fail. rvl To Reverse Look Up a given CIDR IP range. brt To Brute force Domains and Hosts using a given dictionary. srv To Enumerate common SRV Records for a given domain. axfr Test all NS Servers in a domain for misconfigured zone transfers. goo Perform Google search for sub-domains and hosts. snoop To Perform a Cache Snooping against all NS servers for a given domain, testing all with file containing the domains, file given with -D option. tld Will remove the TLD of given domain and test against all TLD's registered in IANA zonewalk Will perform a DNSSEC Zone Walk using NSEC Records. -a Perform AXFR with the standard enumeration. -s Perform Reverse Look-up of ipv4 ranges in the SPF Record of the targeted domain with the standard enumeration. -g Perform Google enumeration with the standard enumeration. -w Do deep whois record analysis and reverse look-up of IP ranges found thru whois when doing standard query. -z Performs a DNSSEC Zone Walk with the standard enumeration. --threads Number of threads to use in Range Reverse Look-up, Forward Look-up Brute force and SRV Record Enumeration --lifetime Time to wait for a server to response to a query. --db SQLite 3 file to save found records. --xml XML File to save found records. --iw Continua bruteforcing a domain even if a wildcard record resolution is discovered. -c, --csv Comma separated value file. -v Show attempts in the bruteforce modes. |
You can download DNSRecon here:
Or read more here.
