The primary goal of the Portspoof program is to enhance your system security through a set of new camouflage techniques which spoof all ports open and also emulate valid services on every port. As a result, any attackers port scan results will become fairly meaningless and will require hours of effort to accurately identify which ports have real services on and which do not.
The tool is meant to be a lightweight, fast, portable and secure addition to any firewall system or security system. The general goal of the program is to make the reconnaissance phase as slow and bothersome for your attackers as possible. This is quite a change to the standard 5s Nmap scan, that will give a full view of your systems running services.
Techniques Used by Portspoof
All configured TCP ports are always open
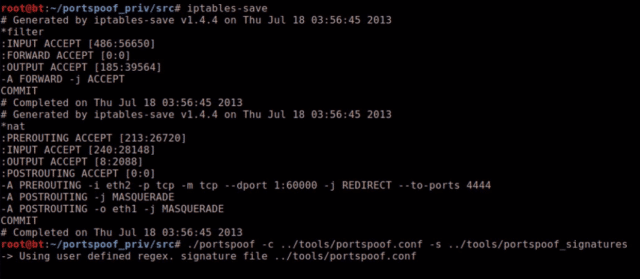
Instead of informing an attacker that a particular port is in a CLOSED or FILTERED state a system running Portspoof will return SYN+ACK for every connection attempt, spoof all ports open.
Result: As a result it is impractical to use stealth (SYN, ACK, etc.) port scanning against your system, since all ports are always reported as OPEN. With this approach it is really difficult to determine if a valid software is listening on a particular port.
Every open TCP port emulates a valid services
Portspoof has a huge dynamic service signature database, that will be used to generate responses to your offenders scanning software service probes.
Scanning software usually tries to determine a service that is running on an open port. This step is mandatory if one would want to identify port numbers on which you are running your services on a system behind the spoofed ports. For this reason, Portspoof will respond to every service probe with a valid service signature, that is dynamically generated based on a service signature regular expression database.
Result: As a result an attacker will not be able to determine which port numbers your system is truly using.
Portspoof Port Spoofing Tool Features
The most important features that Portspoof has:
- Portspoof is a userland software and does not require root privilege
- Binds to just one TCP port per a running instance
- Easily customizable through your iptables rules
- Marginal CPU/memory usage (multithreaded)
- More than 9000 dynamic service signatures are supported
If you choose to, Portspoof can be used as an ‘Exploitation Framework Frontend’, that turns your system into a responsive and aggressive machine. This means exploiting your attackers’ tools and exploits in response to a port scan.
You can download Portspoof here:
Or read more here.

ikobs billy says
This is just awesome