Mr.SIP was developed in Python as a SIP Attack and audit tool which can emulate SIP-based attacks. Originally it was developed to be used in academic work to help developing novel SIP-based DDoS attacks and defence approaches and then as an idea to convert it to a fully functional SIP-based penetration testing tool, it has been redeveloped into the current version.
Mr.SIP – SIP Attack Features
Mr.SIP currently comprises of four sub-modules named SIP-NES, SIP-ENUM, SIP-DAS and SIP-ASP. Since it provides a modular structure to developers, more modules will continue to be added by the authors and it is open to being contributed to by the open-source developer community.
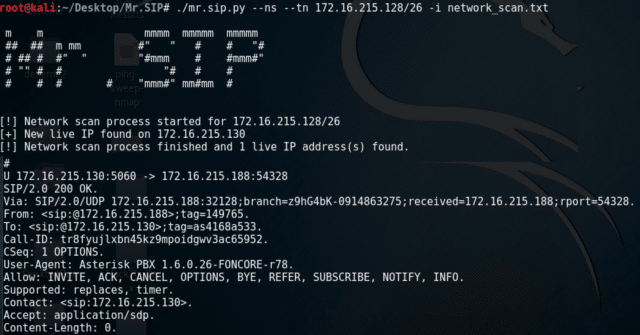
- SIP-NES needs to enter the IP range or IP subnet information. It sends SIP OPTIONS message to each IP addresses in the subnet and according to the responses outputs the potential SIP clients and servers on that subnet.
- SIP-ENUM outputs which SIP users are valid according to the responses in that network by sending REGISTER messages to each client IP addresses on the output of SIP-NES.
- SIP-DAS (DoS Attack Simulator) is a module developed to simulate SIP-based DoS attacks. It comprises four components: spoofed IP address generator, SIP message generator, message sender and scenario player. It needs outputs of SIP-NES (Network Scanner) and SIP-ENUM (Enumerator) along with some pre-defined files.
- SIP-DAS basically generates legitimate SIP INVITE message and sends it to the target SIP component via TCP or UDP. It has three different options for spoofed IP address generation, i.e., manual, random and by selecting spoofed IP address from subnet. IP addresses could be specified manually or generated randomly. Furthermore, in order to bypass URPF filtering, which is used to block IP addresses that do not belong to the subnet from passing onto the Internet, we designed a spoofed IP address generation module. Spoofed IP generation module calculated the subnet used and randomly generated spoofed IP addresses that appeared to come from within the subnet.
There is also:
– ohrwurm – RTP Fuzzing Tool (SIP Phones)
– SIPcrack – SIP Login Dumper & Hash/Password Cracker
– Sipflanker – Locate SIP (VoIP) Device Web Interfaces
– SIP Proxy – VoIP Security Testing Tool
– SIPVicious SIP Scanner – VoIP Hacking Security Auditing Tool
You can download Mr.SIP here:
Or read more here.
