XXE Injection Attacks or XML External Entity vulnerabilities are a specific type of Server Side Request Forgery or SSRF attack relating to abusing features within XML parsers.
The features these attacks go after are widely available but rarely used and when trigged can cause a DoS (Denial of Service) attack and in some cases much more serious escalation like extraction of sensitive data or in worst case scenarios RCE or Remote Code Execution.
What is XML
In computing, Extensible Markup Language (XML) is a markup language that defines a set of rules for encoding documents in a format that is both human-readable and machine-readable.
From: https://en.wikipedia.org/wiki/XML
It’s been replaced in a lot of modern APIs by JSON, but a lot of applications still use XML and/or have XML parsers inside so it’s good to be aware of XXE attacks as a vector.
XML parsers validate data in two main ways, XXE falls within the DTD or Data Type Definition method.
What is an XXE Attack
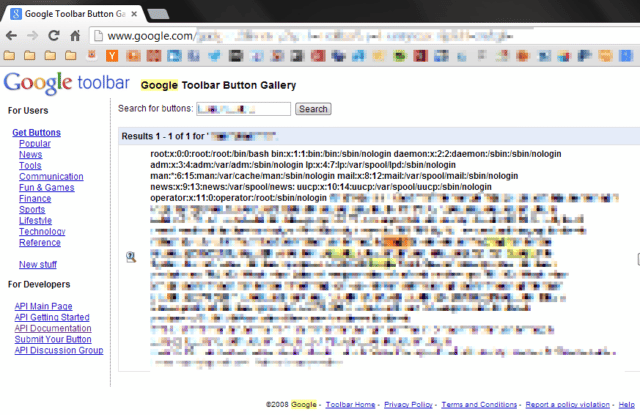
The thing is the XML entities can be defined anywhere, including externally, this is where XXE comes in and can be abused by an attacker by using XML entities to request the execution of certain files or even to return the contents of files if they know the structure of your web application for example.
It’s also worth mentioning, that with some XML parsers, it’s even possible to get directory listings in addition to the contents of a file.
XXE Attack Example
An example would look like this:
Request
|
1 2 3 4 5 6 7 8 9 10 |
POST http://example.com/xml HTTP/1.1 <!DOCTYPE foo [ <!ELEMENT foo ANY> <!ENTITY bar SYSTEM "file:///etc/lsb-release"> ]> <foo> &bar; </foo> |
Response
|
1 2 3 4 5 6 |
HTTP/1.0 200 OK DISTRIB_ID=Ubuntu DISTRIB_RELEASE=16.04 DISTRIB_CODENAME=xenial DISTRIB_DESCRIPTION="Ubuntu 16.04 LTS" |
Obviously this is a simple example, but it could be used to echo /etc/passwd, get secrets from source code repos or execute malicious code (like a web shell) if the attacker has managed to upload something.
You can find out more, in much more depth, here:
Part 1 – What is XML External Entity (XXE)?
Part 2 – XML External Entity (XXE) limitations
Part 3 – Out-of-band XML External Entity (OOB-XXE)
