SSRF or Server Side Request Forgery is an attack vector that has been around for a long time, but do you actually know what it is?
Server Side Request Forgery (SSRF) refers to an attack where in an attacker is able to send a crafted request from a vulnerable web application. SSRF is usually used to target internal systems behind firewalls that are normally inaccessible to an attacker from the external network.
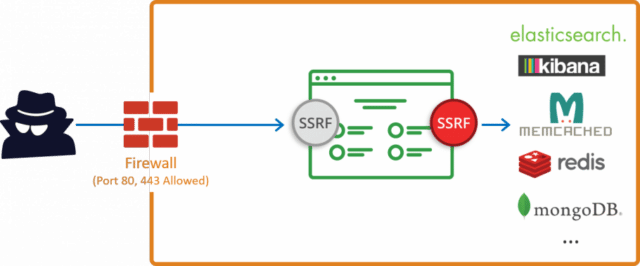
Typically Server Side Request Forgery (SSRF) occurs when a web application is making a request, where an attacker has full or partial control of the request that is being sent. A common example is when an attacker can control all or part of the URL to which the web application makes a request to some third-party service.
There are various things you can use SSRF for such as:
- Scanning other machines within the private network of the vulnerable server that aren’t externally accessible
- Performing Remote File Inclusion (RFI) attacks
- Bypassing firewalls and use the vulnerable server to carry out malicious attacks
- Retrieving server files (including
/etc/passwdetc)
This is example code in PHP that is vulnerable to SSRF:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 |
<?php /** * Check if the 'url' GET variable is set * Example - http://localhost/?url=http://testphp.vulnweb.com/images/logo.gif */ if (isset($_GET['url'])){ $url = $_GET['url']; /** * Send a request vulnerable to SSRF since * no validation is being done on $url * before sending the request */ $image = fopen($url, 'rb'); /** * Send the correct response headers */ header("Content-Type: image/png"); /** * Dump the contents of the image */ fpassthru($image); } |
You can read more from Acunetix here:

bughunter says
https://github.com/cujanovic/SSRF-Testing
Darknet says
Oh that’s nice, thanks!