AWSBucketDump is an AWS S3 Security Scanning Tool, which allows you to quickly enumerate AWS S3 buckets to look for interesting or confidential files. It’s similar to a subdomain brute-forcing tool but is made specifically for S3 buckets and also has some extra features that allow you to grep for delicious files as well as download interesting files if you’re not afraid to quickly fill up your hard drive.
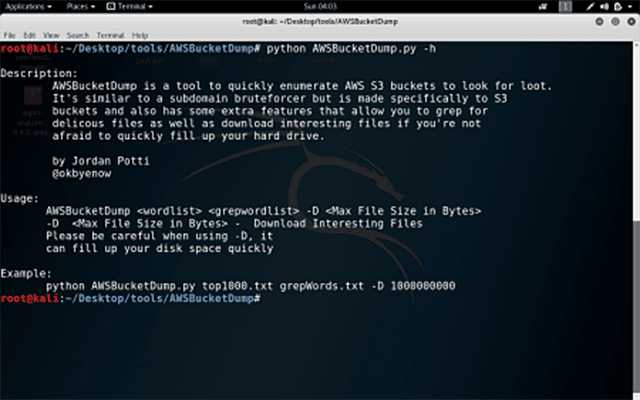
Using the download feature might fill your hard drive up, you can provide a max file size for each download at the command line when you run the tool. Keep in mind that it is in bytes.
By default, there are two threads for checking buckets and two buckets for downloading.
AWSBucketDump Usage
|
1 2 3 4 5 6 7 8 |
usage: AWSBucketDump.py [-h] [-D] [-t THREADS] -l HOSTLIST [-g GREPWORDS] [-m MAXSIZE] -h, --help show this help message and exit -D Download files - this requires significant disk space -d If set to 1 or True, create directories for each host w/ results -t THREADS number of threads -l HOSTLIST -g GREPWORDS Provide a wordlist to grep for -m MAXSIZE Maximum file size to download. |
Example:
|
1 |
python AWSBucketDump.py -l BucketNames.txt -g interesting_Keywords.txt -D -m 500000 -d 1 |
AWSBucketDump S3 Security Tool Requirements
Non-Standard Python Libraries:
- xmltodict
- requests
- argparse
A great accompaniment would be these DNS wordlists from the SecLists repository: Discovery >> DNS
You can download AWSBucketDump here:
Or read more here.
