EvilAbigail is a Python-based tool that allows you run an automated Evil Maid attack on Linux systems, this is the Initrd encrypted root fs attack. An Evil Maid attack is a type of attack that targets a computer device that has been shut down and left unattended.
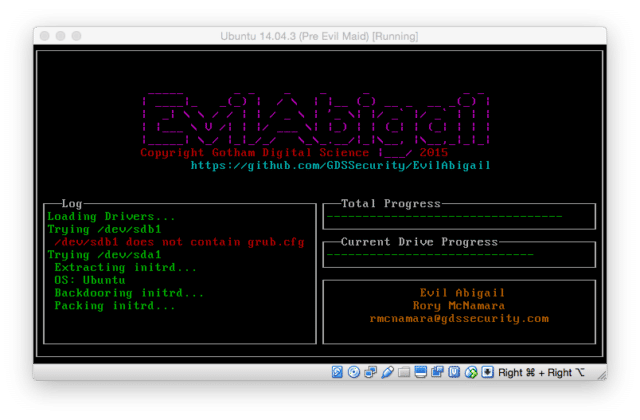
An Evil Maid attack is characterized by the attacker’s ability to physically access the target multiple times without the owner’s knowledge.
Scenarios
- Laptop left turned off with FDE turned on
- Attacker boots from USB/CD/Network
- Script executes and backdoors initrd
- User returns to laptop, boots as normal
- Backdoored initrd loads:
- (Debian/Ubuntu/Kali)
.sofile into/sbin/initon boot, dropping a shell - (Fedora/CentOS)
LD_PRELOAD.sointoDefaultEnviroment, loaded globally, dropping a shell.
- (Debian/Ubuntu/Kali)
Supported Distros
- Ubuntu 14.04.3
- Debian 8.2.0
- Kali 2.0
- Fedora 23
- CentOS 7
You can download EvilAbigail here:
Or read more here.

No one says
You should really provide links to source rather than posting binaries and zip files.
Who really trusts an internet website posting hacking tools without the source?
Darknet says
It’s a zip of the source, not a binary, if you can’t figure out how to access the source from the Github link https://github.com/GDSSecurity/EvilAbigail/archive/master.zip you probably shouldn’t be using it in the first place. If you need a hint, it’s https://github.com/GDSSecurity/EvilAbigail/