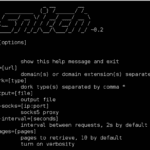
Snitch is an information gathering tool which automates the process for a specified domain. Using built-in dork categories, this tool helps gather specified information domains which can be found using web search engines. It can be quite useful in early phases of penetration tests (commonly called the Information Gathering phase). snitch can identify general information, […]
Archives for June 2017
Fake News As A Service (FNaaS?) – $400k To Rig An Election
This is pretty interesting, the prices for Fake News as a Service have come out after some research by Trend Micro, imagine that you can create a fake celebrity with 300,000 followers for only $2,600. Now we all know this Fake News thing has been going on for a while, and of course, if it’s […]
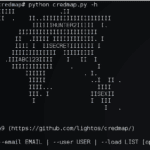
credmap – The Credential Mapper
Credmap is an open source credential mapper tool that was created to bring awareness to the dangers of credential reuse. It is capable of testing supplied user credentials on several known websites to test if the password has been reused on any of these. It is not uncommon for people who are not experts in […]
LazyDroid – Android Security Assessment Tool
Lazydroid is a tool written as a bash script to facilitate some aspects of an Android Security Assessment. Features It provides some common tasks such as: Set the debug flag of an application to true Set the backup flag of an application to true Re-Build the application Re-Sign the application Smart log extraction of an […]
OneLogin Hack – Encrypted Data Compromised
The OneLogin hack is blowing up now it seems like whoever got access can also decrypt encrypted customer data which is just about AS BAD as it can get for a password/identity management service. Now I’m a HUGE supporter of password management tools as I’ve mentioned many times here, so anyone who signed up for […]