This is not the first IoT heavy botnet, Mirai takes that title, the interesting part is the Hajime botnet appears to be benign.
So far no malicious functions have been detected in the codebase, other than the ability to replicate itself and block other malware, Hajime seems to have no DDoS or offensive mechanisms.
Hajime – the “vigilante” IoT worm that blocks rival botnets – has built up a compromised network of 300,000 malware-compromised devices, according to new figures from Kaspersky Lab.
The steadily spreading Hajime IoT worm fights the Mirai botnet for control of easy-to-hack IoT products. The malware is billed as a vigilante-style internet clean-up operation but it might easily be abused as a resource for cyber-attacks, hence a growing concern among security watchers.
Hajime, like Mirai before it, takes advantage of factory-set (default) username and password combinations to brute-force its way into unsecured devices with open Telnet ports. The malware was first discovered [PDF] by security researchers at Rapidity Networks in October 2016. Since then it has spread steadily but inexorably. Most of the targets have turned out to be Digital Video Recorders, followed by webcams and routers, according to Kaspersky Lab.
Hajime avoids several networks, including those of General Electric, Hewlett-Packard, the US Postal Service, the United States Department of Defense, and a number of private networks. Infections had primarily come from Vietnam (over 20 per cent), Taiwan (almost 13 per cent) and Brazil (around 9 per cent).
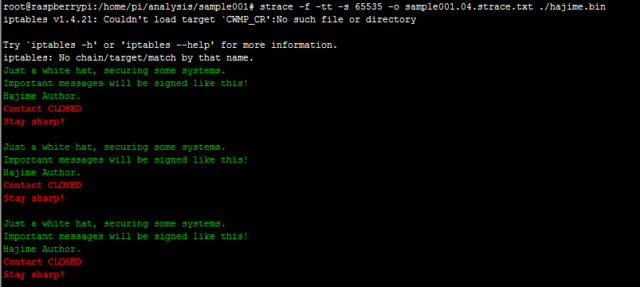
The console messages state the worm was written by a White Hat hacker who is just seeking to protect the systems he/she infects. This seems rather unlikely, but it’s very possible. It might also just be a curious experiment by someone with the skills to use the Mirai code base (which was open-sourced) to do something so widespread.
Either way a DDoS attack from this many hosts would REALLY hurt.
The resiliency of Hajime surpasses Mirai, security researchers say. Features such as a peer-to-peer rather than centralised control network and hidden processes make it harder to interfere with the operation of Hajime (meaning “beginning” in Japanese) than comparable botnets.
Botnets of compromised devices can be harnessed for a variety of cyber-crimes ranging from DDoS attacks on targeted web sites to running credential-stuffing attacks or scanning websites for SQL injection vulnerabilities. The malware – which is not doing anything malign, at least for now – displays a message that says a “white hat” is “securing some systems”. The worm blocks access to ports 23, 7547, 5555, and 5358, common entry points for the rival Mirai worm and other threats.
There is no attacking code or capability in Hajime – only a propagation module. Despite its (current) benign state Hajime is a still concern, not least because the malware’s real purpose remains unknown.
“The most intriguing thing about Hajime is its purpose. While the botnet is getting bigger and bigger, its objective remains unknown. We have not seen its traces in any type of attack or additional malicious activity. Nevertheless, we advise owners of IoT devices to change the password of their devices to one that’s difficult to brute force, and to update their firmware if possible,” said Konstantin Zykov, senior security researcher at Kaspersky Lab.
The worm is blocking the common ports used by Mirai and other IoT threats, so it is aggressive in that aspect.
Other than that, there’s no proof it is actually malicious so we, as usual, will just have to wait and see.
Source: The Register
