RIPS is a tool written in PHP to find vulnerabilities using static source code analysis for PHP web applications. By tokenizing and parsing all source code files RIPS is able to transform PHP source code into a program model and to detect sensitive sinks (potentially vulnerable functions) that can be tainted by user input (influenced by a malicious user) during the program flow. Besides the structured output of found vulnerabilities RIPS also offers an integrated code audit framework for further manual analysis.
Features
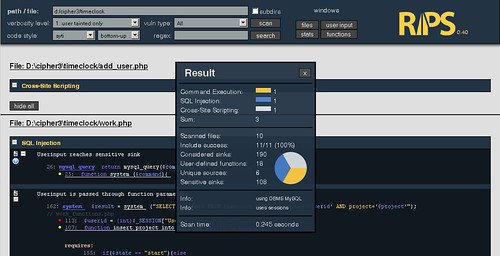
- detect XSS, SQLi, File disclosure, LFI/RFI, RCE vulnerabilities and more
- 5 verbosity levels for debugging your scan results
- mark vulnerable lines in source code viewer
- highlight variables in the code viewer
- user-defined function code by mouse-over on detected call
- active jumping between function declaration and calls
- list of all user-defined functions (defines and calls), program entry points (user input) and scanned files (with includes) connected to the source code viewer
- graph visualization for files and includes as well as functions and calls
- create CURL exploits for detected vulnerabilties with few clicks
- visualization, description, example, PoC, patch and securing function list for every vulnerability
- 7 different syntax highlighting colour schemata
- display scan result in form of a top-down flow or bottom-up trace
- only minimal requirement is a local webserver with PHP and a browser (tested with Firefox)
- regex search function
There are other PHP-centric tools we’ve covered such as:
– RATS – Rough Auditing Tool for Security
– Skavenger – Source Code Auditing Tool!
– SpikeSource Spike PHP Security Audit Tool
If you are interested in more tools of this type you can find our complete list here (which covers various languages) – Code Auditing Tools.
NOTE: The authors have stated that RIPS 0.5 development is abandoned. A complete rewrite is in the works and used as an academic prototype but it is not publicly available yet. So we’ll be keeping an eye on what happens with that.
But for now you can download RIPS here:
Or read more here.

Vlada says
Doesn’t work very well now…
Didn’t recognize simple: $query= “SELECT * FROM tbl where id={$_GET[‘id’]};”;
Looking forward for future revisions.
Darknet says
Yup definitely looking forwards to the new iteration and seeing how different it is.