NINJA-PingU (NINJA-PingU Is Not Just A Ping Utility) is a free open-source high performance network scanner tool for large scale analysis. It has been designed with performance as its primary goal and developed as a framework to allow easy plugin integration.
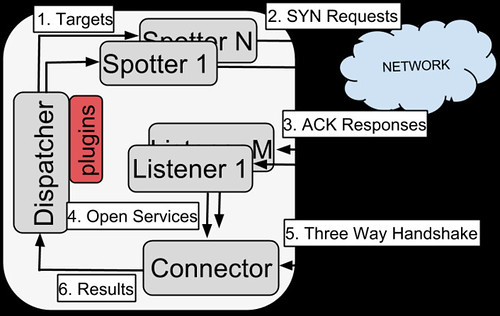
Essentially it’s a high performance, large scale network scanner, the likes of which we haven’t seen for some time. There were a few such projects around in 2008-2009 like Angry IP Scanner & Unicornscan.
It comes out of the box with a set of plugins for services analysisembedded devices identification and to spot backdoors.
NINJA PingU takes advantage of raw sockets to reduce the three-way TCP handshake latency and it’s state. Directly sending IP packets also avoids the TCP stack overhead. It also implements non-blocking networking I/O in the plugin’s interface by means of epoll. Each component is multithreaded and they have built-in caches to minimize synchronization points. In addition, the results persistment operations are buffered to reduce disk writes.
Options
|
1 2 3 4 5 6 7 |
-t Number of sender threads. -p Port scan range. For instance, 80 or 20-80. -d Delay between packages sent (in usecs). -s No service discoverage (less bandwith load, more hosts/time). -m Module to run. For instance, Service. [targets] Can be a single ip or a range (i.e. 0.0.0.0-255.0.0.0). -h Show this help. |
You can download v1.0 here:
Or check out the repo on Github here – https://github.com/OWASP/NINJA-PingU
Or read more here.
