Introducing RAWR (Rapid Assessment of Web Resources). There’s a lot packed in this tool that will help you get a better grasp of the threat landscape that is your client’s web resources. It has been tested from extremely large network environments, down to 5 node networks. It has been fine-tuned to promote fast, accurate, and applicable results in usable formats. RAWR will make the mapping phase of your next web assessment efficient and get you producing positive results faster!
Along the same line as tools like EyeWitness – A Rapid Web Application Triage Tool – and others which are useful for the Information Gathering stage of a pen-test or vulnerability assessment.
Features
- A customizable CSV containing ordered information gathered for each host, with a field for making notes/etc.
- An elegant, searchable, JQuery-driven HTML report that shows screenshots, diagrams, and other information.
- a CSV Treat Matrix for an easy view of open ports across all provided hosts. (Use -a to show all ports.)
- Default password suggestions using a list compiled from several online sources.
- Supports the use of a proxy (Burp, Zap, W3aF)
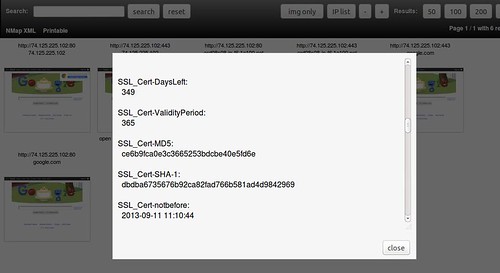
- Captures/stores SSL Certificates, Cookies, and Cross-domain.xml
- Customizable crawl of links within the host’s domain.
- PNG Diagram of all pages found during crawl
- List of links crawled in tiered format.
- List of documents seen for each site.
- Automation-Friendly output (JSON strings)
Requirements
- nmap – at least 6.00 – required for SSL strength assessment
- graphviz – site diagram from crawl (optional)
- python-lxml – parsing xml & html
- python-pygraphviz – site layout from crawl (optional)
- phantomJS – tested with 1.9.1, can be downloaded/installed in local folder during –check-install
You can download RAWR 1.1 here by checking it out from Bitbucket:
|
1 |
git clone https://bitbucket.org/al14s/rawr.git |
Or read more here.
