inspathx is a tool that uses local source tree to make requests to the URL and searches for path inclusion (Full Path Disclosure) error messages. It’s a very common problem in PHP web applications that crops up a lot. PHP Web application developers sometimes fail to add safety checks against authentications, file inclusion etc and […]
Archives for September 2010
JailBreaking AppleTV Running on iOS 4.1 – iPad/iPhone 4 Jailbreak Soon?
Posts about the latest Jailbreak exploit/software for the new Apple devices are always pretty popular and this looks like it might turn out to be pretty interesting. It seems like at the moment the latest iOS update has been cracked for iPod Touch and earlier iPhones (3GS) but there’s no working Jailbreak at the moment […]
TA-Mapper v1.1 – Time and Attack Mapper – Effort Estimator For Pen-Testing
We wrote about this tool back in January 2009 when it was first released, recently v1.1 has become available for download. Time and Attack Mapper (alternatively known as TA-Mapper) is an effort estimator tool for blackbox security assessment (or Penetration Testing) of applications. This tool provides more accurate estimation when compared to rough estimation. Penetration […]
Microsoft Warns Of ASP.Net Vulnerability In The Wild – Cryptographic Padding Attack
There seems to be a fairly serious attack being exploited in the wild that targets vulnerable ASP.Net web applications, so far there is a temporary fix but no official announcement on when a patch will be issued. The next scheduled patches should be pushed out on October 12th. If you had set up your server […]
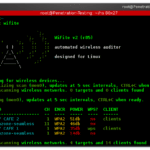
wifite – Mass Wifi WEP / WPA Key Cracking Tool
wifite is created to attack multiple WEP and WPA encrypted networks at the same time. This tool is customizable to be automated with only a few arguments and can be trusted to run without supervision. It’s a great tool to script into part of a toolkit for Wifi security assessments and is a handy wifi […]