httprecon is a tool for advanced web server fingerprinting, similar to httprint that we mentioned previously.
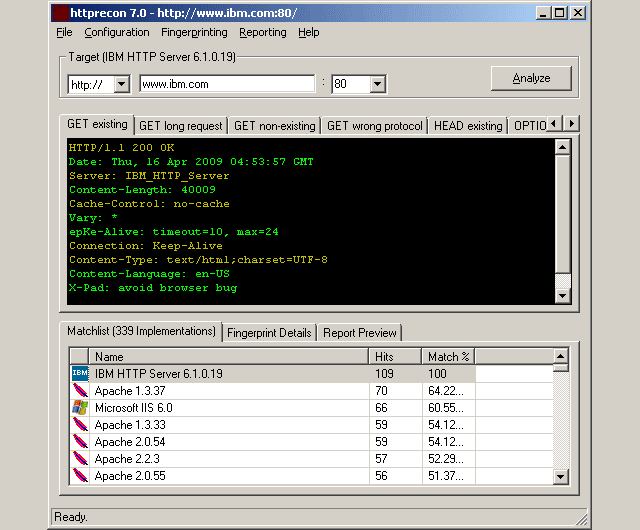
The httprecon project is doing some research in the field of web server fingerprinting, also known as http fingerprinting. The goal is the highly accurate identification of given httpd implementations. This is very important within professional vulnerability analysis.
Besides the discussion of different approaches and the documentation of gathered results also an implementation for automated analysis is provided. This software shall improve the easiness and efficiency of this kind of enumeration. Traditional approaches as like banner-grabbing, status code enumeration and header ordering analysis are used. However, many other analysis techniques were introduced to increase the possibilities of accurate web server fingerprinting.
Besides the well-known enumeration of http response status codes and header-ordering several other fingerprinting mechanisms were introduced. For example the capitalization of header lines, the use of spaces and the structure of ETag values (e.g. length and quotes).
Features of httprecon – Advanced Web Server Fingerprinting tool
These are the main features of the current implementation of httprecon which makes this solution better than other tools of this kind:
- Many test-cases: There are nine test-cases possible
- HTTPS/SSL support: Secure web servers can be tested too
- Advanced result analysis: Different methods for the analysis of results is provided
- Many fingerprint details: The analysis is based on many fingerprint elements
- Plaintext Database: The fingerprint data is saved in a file-based plaintext database
- Fingerprint Wizard: Fingerprints can be saved and updated within the GUI
- IDS evasion mechanism: The configuration settings allow to use IDS evasion mechanisms
- Reporting: XML, HTML and TXT reporting is provided for professional testers
- Autoupdate: An autoupdate feature informs about new releases
- Open-source (GPLv3): Everyone can improve the application for themselves
This increases the number of fingerprints to distinguish the given implementation. Thus, the accuracy of the fingerprinting series is very high. Theoretically, httprecon 1.x is able to generate approx. 198 fingerprint atoms per full scan run (usually between 80 and 120 are given).
You can download httprecon 7.3 here:
Source (VB6) – httprecon-7.3.zip
Or read more here.

lars says
Ok… what I see in my HTTP HEADER:
Server: Apache/1.3.33 (Unix) PHP/4.2.1
Which I know is correct and not faked.
httprecon is 100% sure it’s an Apache 1.3.37, with 96% it could also be 1.3.26.
With 94% it could even possibly be 1.3.33 (yay \o/).
Same with Apache2, doesn’t get it right even if it’s written in the header.
Well, better than nothing and I bet it’s perfect against IIS :D
Pantagruel says
@lars
True, httprecon is slightly off.
Running Apache 2 2.2.3 here and httprecon thinks the best guess is 2.0.59 (100%) and 2.2.3 is second (98,27%) eventhough I haven’t touched the info apache2 spills out when queried.
It does the router/modem combo right, but it is somewhat of a laugh to see httprecon consider IIS6 (76%) to be a viable option for the Zyxell box as well.
Darknet says
Hmm that’s interesting guys, is httprint still more accurate? Even though it’s outdated.
Pantagruel says
@Darknet
httprint is rather outdated so I wouldn’t expect any better result when comparing to the newer httprecon.
The windows version gave me
…snip…
Apache/2.0.x: 140 84.34
Apache/1.3.[4-24]: 132 68.91
Apache/1.3.27: 131 67.12
Apache/1.3.26: 130 65.36
Apache/1.3.[1-3]: 127 60.28
TUX/2.0 (Linux): 123 53.90
Apache/1.2.6: 117 45.20
…snip…
on the same machine as above, so the result is worse.
Both httprint and httprecon where right about the fact that the machine is running SuSe (as advertised in the http header).
zupakomputer says
Is that happening because the db doesn’t have correct matches for all the Apache versions or does Apache recognise such queries and do a bit of masking as a built in feature?
Or if not, maybe it’d be better not doing as many fingerprints on well-known server versions, as in perhaps the amount of them throws in some inaccurate stats so lowers the percentages.
Does it let you run queries for unhidden and unspoofed servers, and also run a separate set for a return on the best guess if the server is set-up to mask itself?
James C says
httprint gave me more accurate results on 10 server’s i tested.
There seem to be 95% chance that httprecon will give you the wrong answers.
httprecon wrong answers rate for me is 99%
Pantagruel says
@zupakomputer
Indeed it appears to be the age of the db the generated finger prints are checked against. Haven’t tried any of your other mentioned possibilities.
Darknet says
I don’t it’s the age of the database, I think the point is it uses all methods but the banner given as that can be easily changed or spoofed to something else.
So even if you change your banner to IIS 8.1 it’ll still come back the same ‘fairly’ accurate results.
It’s going on behaviour rather than just the banner, it’s an interesting idea but perhaps could be better implemented.
zupakomputer says
Might be handy then for it to do a banner read and return that result, then run the other checks if in the event the banner is spoofed, so you can check both results beside one another and get a better idea if it really is spoofed.
Marc Ruef says
Hello,
I am the developer of httprecon and I am highly interested in the discussion on this page. Therefore, I would like to say something about the “missing” accuracy. During the developement process of httprecon I tried to gather all possible data of httpd implementations. This means I was searching through Google and looking for some new pages. It is no surprise that I was not able to find all possible implementations and versions.
Sometimes I only found one example and fingerprinted it. If there is a weird configuration or an intermediate web proxy used, the current fingerprint is not so accurate. This is why you will get some 97 % results even the implementation is announced in the Server line clearly. See the documentation at http://www.computec.ch/projekte/httprecon/?s=documentation for more details.
However, the big advantage of httprecon is, a) that the accuracy becomes higher as more implementations are fingerprinted (use the save and upload feature in the software every time!) and b) it is able to “ignore” manipulations to hide the implementation (e.g. changeing the banner). Other http fingerprinting tools are more static and might lose track if there is some evasion techniques used.
The current releases (up to 4.3) do not use any match weight during fingerprinting. This means every hit generates 1 point. In future releases an individual weight for different matches shall be introduced. E.g. the order of the headers is more accurate than the string of the Server line. This would increase the accuracy further more.
Regards,
Marc
PS: I am currently working on a fork project with the title telnetrecon. Further details at http://www.computec.ch/projekte/telnetrecon/
Pantagruel says
@Mark Ruef
Thanks for the added info, so we can all pitch in by uploading the data regarding our fingerprinted machines.
zupakomputer says
I did that at p0f recently – it didn’t recognise it was Suse I was using (on the last Virtual Machine release, within XP) so I used the form there to send in the details.
Maybe good for a cross-reference, collate all these databases together for all the more accuracy.