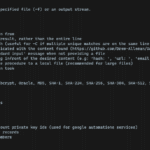
DataSurgeon (ds) is a versatile tool designed to Extract Sensitive Information (PII) From Logs, it’s intended to be used for incident response, penetration testing, and CTF challenges.
penetration-testing
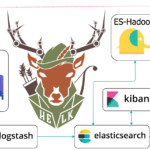
HELK – Open Source Threat Hunting Platform
The Hunting ELK or simply the HELK is an Open-Source Threat Hunting Platform with advanced analytics capabilities such as SQL declarative language, graphing, structured streaming, and even machine learning via Jupyter notebooks and Apache Spark over an ELK stack. This project was developed primarily for research, but due to its flexible design and core components, […]
Yuki Chan – Automated Penetration Testing Tool
Yuki Chan is an Automated Penetration Testing Tool that carries out a whole range of standard security auditing tasks automatically. It’s highly recommended to use this tool within Kali Linux OS as it already contains all the dependencies. This tool is only designed for Linux OS so if you are not using Linux OS it […]
PenTools – Penetration Testing Tools Bundle
PenTools is a bundle of Python and Bash penetration testing tools for the recon and information gathering stage of a PT or VA. They are fairly simple scripts but might be interesting if you are new and want to see how some things are done, or how things can be automated using Python or Bash. […]
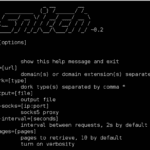
snitch – Information Gathering Tool Via Dorks
Snitch is an information gathering tool which automates the process for a specified domain. Using built-in dork categories, this tool helps gather specified information domains which can be found using web search engines. It can be quite useful in early phases of penetration tests (commonly called the Information Gathering phase). snitch can identify general information, […]