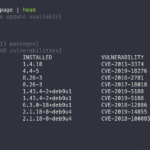
Grype is a vulnerability scanner for container images and filesystems with an easy to install binary that supports the packages for most major *nix based operating systems. Features of Grype Vulnerability Scanner For Container Images & Filesystems Scan the contents of a container image or filesystem to find known vulnerabilities and find vulnerabilities for major […]
APT-Hunter – Threat Hunting Tool via Windows Event Log
APT-Hunter is a threat hunting tool for windows event logs made from the perspective of the purple team mindset to provide detection for APT movements hidden in the sea of windows event logs. This will help you to decrease the time to uncover suspicious activity and the tool will make good use of the windows […]
GitLab Watchman – Audit Gitlab For Sensitive Data & Credentials
GitLab Watchman is an application that uses the GitLab API to audit GitLab for sensitive data and credentials exposed internally – this includes code, commits, wiki pages and more. GitLab Watchman searches GitLab for internally shared projects and looks at: Code Commits Wiki pages Issues Merge requests Milestones For the following data: GCP keys and […]
GKE Auditor – Detect Google Kubernetes Engine Misconfigurations
GKE Auditor is a Java-based tool to detect Google Kubernetes Engine misconfigurations, it aims to help security and development teams streamline the configuration process and save time looking for generic bugs and vulnerabilities. The tool consists of individual modules called Detectors, each scanning for a specific vulnerability. Installing and Using GKE Auditor to Detect Google […]
zANTI – Android Wireless Hacking Tool Free Download
zANTI is an Android Wireless Hacking Tool that functions as a mobile penetration testing toolkit that lets you assess the risk level of a network using your mobile device for free download. This easy to use mobile toolkit enables IT Security Administrators to simulate an advanced attacker to identify the malicious techniques they use in […]