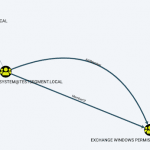
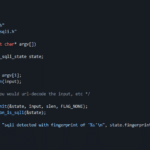
assetfinder is a Go-based tool to find related domains and subdomains that are potentially related to a given domain from a variety of sources including Facebook, ThreatCrowd, Virustotal and more. assetfinder uses a variety of sources including those in the infosec space and social networks which can give relevant info: crt.sh certspotter hackertarget threatcrowd wayback […]
Karkinos – Beginner Friendly Penetration Testing Tool
Karkinos is a light-weight Beginner Friendly Penetration Testing Tool, which is basically a ‘Swiss Army Knife’ for pen-testing and/or hacking CTF’s. Karkinos Beginner Friendly Penetration Testing Tool Features Encoding/Decoding characters Encrypting/Decrypting text or files Reverse shell handling Cracking and generating hashes How to Install Karkinos Beginner Friendly Penetration Testing Tool Dependencies are: Any server capable […]
Aclpwn.Py – Exploit ACL Based Privilege Escalation Paths in Active Directory
Aclpwn.py is a tool that interacts with BloodHound to identify and exploit ACL based privilege escalation paths. It takes a starting and ending point and will use Neo4j pathfinding algorithms to find the most efficient ACL based privilege escalation path. Features of Aclpwn.Py Exploit ACL Based Privilege Escalation Paths in Active Directory Aclpwn.Py currently has […]
Vulhub – Pre-Built Vulnerable Docker Environments For Learning To Hack
Vulhub is an open-source collection of pre-built vulnerable docker environments for learning to hack. No pre-existing knowledge of docker is required, just execute two simple commands and you have a vulnerable environment. Features of Vulhub Pre-Built Vulnerable Docker Environments For Learning To Hack Vulhub contains many frameworks, databases, applications, programming languages and more such as: […]
LibInjection – Detect SQL Injection (SQLi) and Cross-Site Scripting (XSS)
LibInjection is a C library to Detect SQL Injection (SQLi) and Cross-Site Scripting (XSS) through lexical analysis of real-world Attacks. SQLi and other injection attacks remain the top OWASP and CERT vulnerability. Current detection attempts frequently involve a myriad of regular expressions which are not only brittle and error-prone but also proven by Hanson and […]