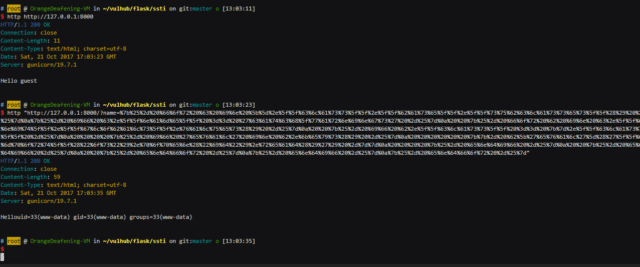
Vulhub is an open-source collection of pre-built vulnerable docker environments for learning to hack. No pre-existing knowledge of docker is required, just execute two simple commands and you have a vulnerable environment.
Features of Vulhub Pre-Built Vulnerable Docker Environments For Learning To Hack
Vulhub contains many frameworks, databases, applications, programming languages and more such as:
- Drupal
- ffmpeg
- CouchDB
- ActiveMQ
- Glassfish
- Joombla
- JBoss
- Kibana
- Laravel
- Rails
- Python
- Tomcat
And many, many more.
To use Vulhub Pre-Built Vulnerable Docker Environments For Learning To Hack
Install the docker/docker-compose on Ubuntu 20.04:
|
1 2 3 4 5 6 7 8 9 10 11 |
# Install pip curl -s https://bootstrap.pypa.io/get-pip.py | python3 # Install the latest version docker curl -s https://get.docker.com/ | sh # Run docker service systemctl start docker # Install docker compose pip install docker-compose |
It is recommended to use a VPS of at least 1GB memory to build a vulnerability environment. The your-ip mentioned in the documentation refers to the IP address of your VPS. If you are using a virtual machine, it refers to your virtual machine IP, not the IP inside the docker container.
You can download Vulhub by:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
# Download project wget https://github.com/vulhub/vulhub/archive/master.zip -O vulhub-master.zip unzip vulhub-master.zip cd vulhub-master # Enter the directory of vulnerability/environment cd flask/ssti # Compile environment docker-compose build # Run environment docker-compose up -d |
Or read more here.
