Scallion is a GPU-driven Onion Hash Generator written in C#, it lets you create vanity GPG keys and .onion addresses (for Tor’s hidden services) using OpenCL. Scallion runs on Mono (tested in Arch Linux) and .NET 3.5+ (tested on Windows 7 and Server 2008) Scallion was used to find collisions for every 32bit key id […]
Search Results for: gpu
IGHASHGPU – GPU Based Hash Cracking – SHA1, MD5 & MD4
IGHASHGPU is an efficient and comprehensive command line GPU based hash cracking program that enables you to retrieve SHA1, MD5 and MD4 hashes by utilising ATI and nVidia GPUs. It even works with salted hashes making it useful for MS-SQL, Oracle 11g, NTLM passwords and others than use salts. IGHASHGPU is meant to function with […]
SHA-1 Password Hashes Cracked Using Amazon EC2 GPU Cloud
It’s not the first time someone has pulled this off, back in November 2009 we wrote about Using Cloud Computing To Crack Passwords – Amazon’s EC2. Add that with a story way back from 2007 – Graphics Cards – The Next Big Thing for Password Cracking? – and you’ve got yourself an interesting combo with […]
CUDA-Multiforcer – GPU Powered High Performance Multihash Brute Forcer
The Cryptohaze Multiforcer is a high performance multihash brute forcer with support for per-position character sets, and very good performance scaling when dealing with large hash lists. As an example, on a list of 10 hashes, the Cryptohaze Multiforcer achieves 390M steps per second on a GTX260/[email protected] card. On a list of 1.4 million hashes […]
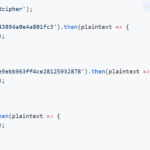
dcipher – Online Hash Cracking Using Rainbow & Lookup Tables
dcipher is a JavaScript-based online hash cracking tool to decipher hashes using online rainbow & lookup table attack services. The capacity to programmatically crack passwords is also a function of the number of possible passwords per second which can be checked. If a hash of the target password is available to the attacker, this number […]