You all probably remember the big kerfuffle that occurred after RSA got hacked, it was widely assumed that the SecurID system was compromised somehow and could not be relied on. We reported about it in the article – RSA Silent About Compromise For 7 Days – Assume SecurID Is Broken – where we questioned their […]
Archives for May 2011
Sniffjoke 0.4.1 Released – Anti-sniffing Framework & Tool For Session Scrambling
SniffJoke is an application for Linux that handle transparently your TCP connection, delaying, modifying and injecting fake packets inside your transmission, make them almost impossible to be correctly read by a passive wiretapping technology (IDS or sniffer). An Internet client running SniffJoke injects in the transmission flow some packets able to seriously disturb passive analysis […]
Sony PlayStation Network (PSN) Reopens In Asia
Finally! My friends over in this hemisphere can finally stop whining and get back on PSN! We’ve been covering this whole Sony Hack quite extensively over the past few weeks and this should be the final part of the network coming back online. Asia is the last segment of the PlayStation Network to come back […]
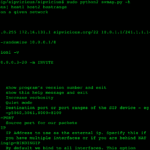
SIPVicious SIP Scanner – VoIP Hacking Security Auditing Tool
SIPVicious SIP Scanner is a suite of tools that can be used to audit SIP based VoIP systems. Why the name? Because the tools are not exactly the nicest thing on earth next to a SIP device. Features for SIP Hacking with SIPVicious It currently consists of five tools: svmap – This is a sip […]
Hotmail Exploit Has Been Silently Stealing E-mail
We haven’t reported a whole lot about Hotmail over the years, probably because since Gmail took over – Hotmail has mostly taken a backseat. The most recent report we had was about SSL and how Hotmail Always-On Encryption Breaks Microsoft’s Own Apps. The latest news is there has been a nasty bug in Hotmail for […]