[ad] WSFuzzer is a fuzzing tool targetting HTTP and SOAP based web services. The program currently targets Web Services. In the current version HTTP based SOAP services are the only supported targets. This tool was created based on, and to automate, some of the manual SOAP pen testing work we perform. This tool is NOT […]
Archives for March 2008
Mac owned on 2nd day of Pwn2Own hack contest
[ad] I have been following this contest and was wondering which OS would be first to fall (if any) seen as though they were all fully patched and the latest versions. For those that don’t know Pwn2Own is a contest at CanSecWest open to anyone to hack a Windows, Linux or Mac OSX box with […]
Webshag v1.00 – Web Server Auditing Tool (Scanner and File Fuzzer)
[ad] Webshag is a multi-threaded, multi-platform web server audit tool. Written in Python, it gathers commonly useful functionalities for web server auditing like website crawling, URL scanning or file fuzzing. Webshag can be used to scan a web server in HTTP or HTTPS, through a proxy and using HTTP authentication (Basic and Digest). In addition […]
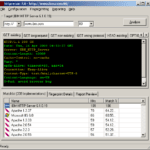
httprecon – Advanced Web Server Fingerprinting
httprecon is a tool for advanced web server fingerprinting, similar to httprint that we mentioned previously. The httprecon project is doing some research in the field of web server fingerprinting, also known as http fingerprinting. The goal is the highly accurate identification of given httpd implementations. This is very important within professional vulnerability analysis. Besides […]
Hacking Windows NT Through IIS & FTP
[ad] This is another selection from the Old Skool Philes, I like these as they tend to generate some good discussion and they are a good introduction to newcomers to hacking on the mindset and workflow of getting access to a box. The exact methods may not work, but we aren’t here to train script […]