Google is ramping up its campaign against HTTP only sites and is going to mark ALL Non-HTTPS sites insecure in July 2018 with the release of Chrome 68. It’s a pretty strong move, but Google and the Internet, in general, has been moving in this direction for a while.
It started with suggestions, then forced SSL on all sites behind logins, then mixed-content warnings, then showing HTTP sites are not-secured and now it’s going to be outright marked as insecure.
Three years ago, Google’s search engine began favouring in its results websites that use encrypted HTTPS connections.
Sites that secure their content get a boost over websites that used plain-old boring insecure HTTP. In a “carrot and stick” model, that’s the carrot: rewarding security with greater search visibility.
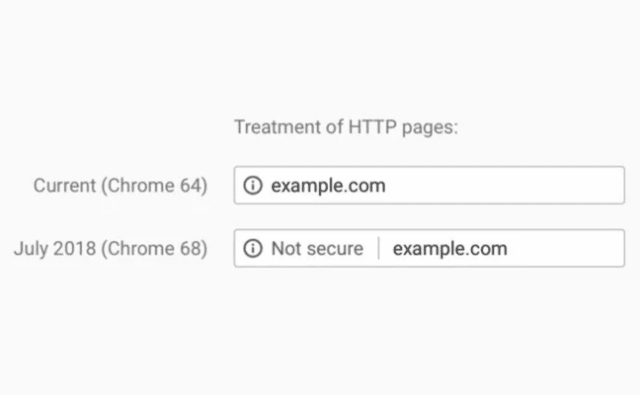
Later this year comes the stick. This summer, Google will mark non-HTTPS websites as insecure in its Chrome browser, fulfilling a plan rolled out in September 2016.
Starting with Chrome 68, due to hit the stable distribution channel on July 2018, visiting a website using an HTTP connection will prompt the message “Not secure” in the browser’s omnibox – the display and input field that accepts both URLs and search queries.
“Chrome’s new interface will help users understand that all HTTP sites are not secure, and continue to move the web toward a secure HTTPS web by default,”
I’m glad I updated this site to SSL before it became absolutely critical, and to be honest with Google Cloud, Amazon AWS and Lets Encrypt offering SSL termination for free, there’s no real excuse not to be on SSL anymore.
– Introducing managed SSL for Google App Engine
– New – AWS Certificate Manager – Deploy SSL/TLS-Based Apps on AWS
– Getting Started – Let’s Encrypt – Free SSL/TLS Certificates
Because Chrome holds something like 56 percent of the global browser market share across mobile and desktop platforms, Google’s name-and-shame label is likely to be noticed by a great many Chrome users and by any websites those fans no longer visit due to security concerns.
While many websites will be affected, plenty are already in compliance. According to Google, 81 of the top 100 websites use HTTPS by default, over 68 percent of Chrome traffic on Android and Windows occurs over HTTPS, and over 78 percent of Chrome traffic on Chrome OS and macOS and iOS travels securely.
Google offers a free security auditing tool called Lighthouse that can help developers identify which website resources still load using insecure HTTP.
The Chocolate Factory’s shunning scheme follows a similar tack the company has taken to issue warnings to websites that rely on dodgy Symantec digital certificates.
I would imagine similar standards are going to be pushed out across the other browsers given the time and the fact Google is still the biggest search engine, they define how the web reacts.
Make sure your SSL install is secure using these:
– TLSSLed v1.2 – Evaluate The Security Of A Target SSL Or TLS (HTTPS) Web Server Implementation
– sslscan Download – Detect SSL Versions & Cipher Suites (Including TLS)
The official blog by Google on this is here:
I personally think this is a step in the right direction and wonder why only 81 of the top 100 sites are on SSL.
Source: The Register
