dorkbot is a modular command-line tool for Google dorking, which is performing vulnerability scans against a set of web pages returned by Google search queries in a given Google Custom Search Engine.
How dorkbot works
It is broken up into two sets of modules:
- Indexers – modules that issue a search query and return the results as targets
- Scanners – modules that perform a vulnerability scan against each target
Targets are stored in a local database file upon being indexed. Once scanned, any vulnerabilities found by the chosen scanner are written to a standard JSON report file. Indexing and scanning processes can be run separately or combined in a single command.
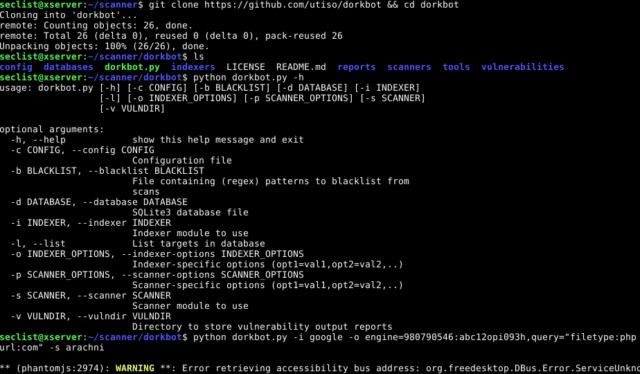
dorkbot Google Vulnerability Scanner Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 |
usage: dorkbot.py [-h] [-c CONFIG] [-b BLACKLIST] [-d DATABASE] [-i INDEXER] [-l] [-o INDEXER_OPTIONS] [-p SCANNER_OPTIONS] [-s SCANNER] [-v VULNDIR] optional arguments: -h, --help show this help message and exit -c CONFIG, --config CONFIG Configuration file -b BLACKLIST, --blacklist BLACKLIST File containing (regex) patterns to blacklist from scans -d DATABASE, --database DATABASE SQLite3 database file -i INDEXER, --indexer INDEXER Indexer module to use -l, --list List targets in database -o INDEXER_OPTIONS, --indexer-options INDEXER_OPTIONS Indexer-specific options (opt1=val1,opt2=val2,..) -p SCANNER_OPTIONS, --scanner-options SCANNER_OPTIONS Scanner-specific options (opt1=val1,opt2=val2,..) -s SCANNER, --scanner SCANNER Scanner module to use -v VULNDIR, --vulndir VULNDIR Directory to store vulnerability output reports |
Example:
|
1 |
./dorkbot.py -i google -o engine=012345678901234567891:abc12defg3h,query="filetype:php inurl:id" |
The scanner module also needs:
– Arachni – Web Application Security Scanner Framework
– Wapiti – Web Application Scanner / Black-box testing
You can download dorkbot here:
Or read more here.
