Cr3dOv3r is a fairly simple Python-based set of functions that carry out the prelimary work as a credential reuse attack tool.
You just give the tool your target email address then it does two fairly straightforward (but useful) jobs:
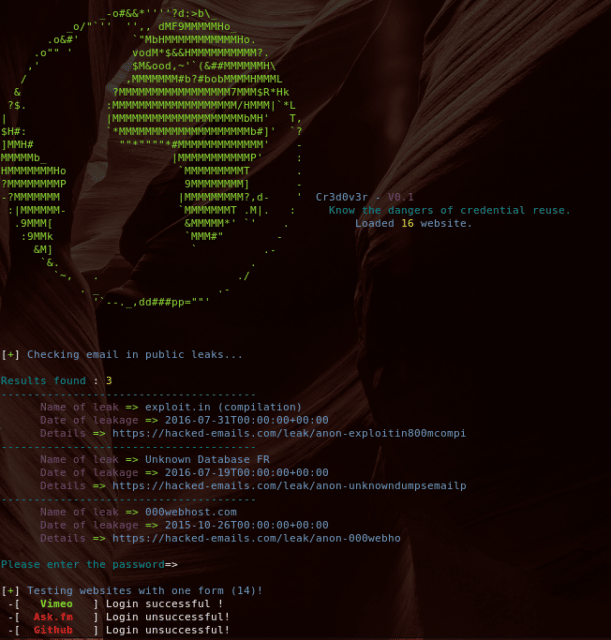
- Search for public leaks for the email and if it any, it returns with all available details about the leak (Using hacked-emails site API).
- Then you give it this email’s old or leaked password then it checks this credentials against 16 websites (ex: facebook, twitter, google…) and notifies of any successful logins.
So how would this Credential Reuse Attack Tool work?
Just imagine this scenario:
- You check a targeted email with this tool.
- The tool finds the email address involved in a leak so you open the leakage link.
- You get the leaked password after searching the leak details.
- You return to the tool and enter the password to check if there’s any website the user uses the same password in it.
- PROFIT
How to use Cr3dOv3r for a Credential Reuse Attack
|
1 2 3 4 5 6 7 |
usage: Cr3d0v3r.py [-h] email positional arguments: email Email/username to check optional arguments: -h,--help show this help message and exit |
Another useful tool could be:
– credmap – The Credential Mapper
You can download Cr3dOv3r here:
Or read more here.
