The Malaysia Telco Hack has been blowing up in the news with over 46 Million Records being leaked including IMEI numbers, SIM card details, serial numbers and home addresses.
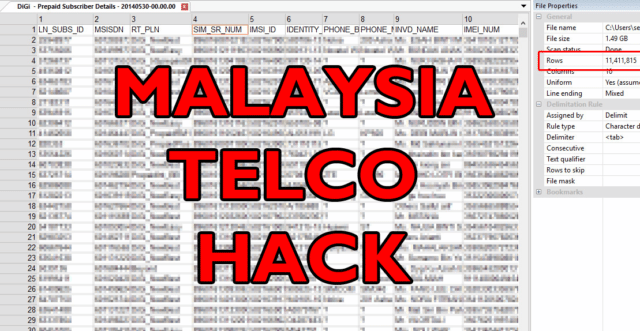
This is an interesting one for me as I live in Malaysia, so this Malaysia Telco Hack was big news over here, especially seen as though from the numbers it looks to affect pretty much every single person in the country (and many more than once with a popular of 31 million).
It’s also a pretty big leak, even on the global scale with the recent large with other recent high-profile cases like Taringa hack being 27 million, Equifax hack at 143 Million or more and Time Warner Cable hack with a paltry 4 Million.
The personal data of millions of Malaysians has been swiped by hackers who raided government servers and databases at a dozen telcos in the southeast Asia nation.
Information on 46.2 million cellphone accounts was slurped from Malaysians telecoms providers. To put that in context, the population of Malaysia is 31.2 million; obviously, some people have more than one number.
The stolen telco records include people’s mobile phone numbers, SIM card details, device serial numbers, and home addresses, all of which are useful to identity thieves and scammers. Some 80,000 medical records were also accessed during the hacking spree, and government websites as well as Jobstreet.com were attacked and infiltrated, too, we’re told.
The Malaysian Communications and Multimedia Commission, along with the police, are probing the computer security breaches. DiGi.Com and Celcom Axiata are among the dozen compromised telcos assisting investigators.
The breach was first seen on LowYat.net a local technology forum, but the article was taken down very shortly afterwards by the Multimedia Commission of Malaysia (MCMC).
The data itself appeared on the darknet selling the files for an undisclosed amount of Bitcoin, which is a fairly normal thing to happen to leaked data although it seems the hack (or hacks?) took place some time in 2014.
The intrusions were first reported by Malaysian news site lowyat.net, which spotted, in the middle of last month, a mystery scumbag trying to flog the stolen data for Bitcoins.
Malaysian officials confirmed this week that nearly 50 million mobile phone account records were accessed by hackers unknown. The authorities also warned that people’s private data was stolen from the Malaysian Medical Council, the Malaysian Medical Association, the Academy of Medicine, the Malaysian Housing Loan Applications body, the Malaysian Dental Association, and the National Specialist Register of Malaysia.
It’s believed the systems were actually hacked as far back as 2014, The Star reported.
Incredible as it may seem there’s at least a couple of precedents for a huge chunk of the population of an entire country getting caught up in a database security breach.
Apart from telcos there appeared to be data from some other large Malaysian corporations including Jobstreet, the Malaysian Medical Council, Malaysian Housing Loan Applications, the Dental Association and some others.
And those were big too with the Jobstreet database alone having almost 17 Million rows of customer information including address and phone number for many people, which seemed to date back slightly further to 2012-2013.
The Malaysia Telco hack data included every major telco and MVNO in the country, Celcom, DiGi, Maxis, Umobile, Friendi, Tunetalk, Redtone, XOX, Altel, PLDT and EnablingAsia.
It’s very likely the data has been for sale for quite some time on the darknet markets, someone probably bought it cheaply as it’s quite old and exposed it by trying to make a quick buck on a clearnet forum.
Source: The Register
