scanless is a Python-based command-line utility that functions as a public port scan scraper, it can use websites that can perform port scans on your behalf.
This is useful for early stages of penetration tests when you’d like to run a port scan on a host without having it originate from your IP address.
Public Port Scanners
- yougetsignal
- viewdns
- hackertarget
- ipfingerprints
- pingeu
Dependencies
scanless requires the requests and bs4 libraries to run, install with pip.
Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
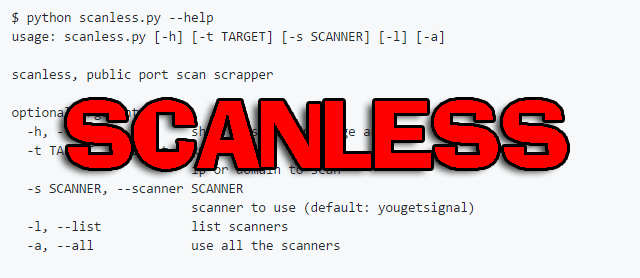
$ python scanless.py --help usage: scanless.py [-h] [-t TARGET] [-s SCANNER] [-l] [-a] scanless, public port scan scrapper optional arguments: -h, --help show this help message and exit -t TARGET, --target TARGET ip or domain to scan -s SCANNER, --scanner SCANNER scanner to use (default: yougetsignal) -l, --list list scanners -a, --all use all the scanners |
Example:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 |
python scanless.py --list Scanner Name | Website ---------------|------------------------------ yougetsignal | http://www.yougetsignal.com viewdns | http://viewdns.info hackertarget | https://hackertarget.com ipfingerprints | http://www.ipfingerprints.com pingeu | http://ping.eu $ python scanless.py -s viewdns -t scanme.nmap.org Running scanless... ------- viewdns ------- PORT STATE SERVICE 21/tcp closed ftp 22/tcp open ssh 23/tcp closed telnet 25/tcp closed smtp 53/tcp closed dns 80/tcp open http 110/tcp closed pop3 139/tcp closed netbios 143/tcp closed imap 443/tcp closed https 445/tcp closed smb 1433/tcp closed mssql 1521/tcp closed oracle 3306/tcp closed mysql 3389/tcp closed rdp ----------------------- |
You can download scanless here:
Or read more here.
