Cyborg Hawk Linux is a Ubuntu based Linux Hacking Distro also know as a Pentesting Linux Distro it is developed and designed for ethical hackers and penetration testers. Cyborg Hawk Distro can be used for network security and assessment and also for digital forensics. It also has various tools suited to the testing of Mobile Security and Wireless infrastructure.
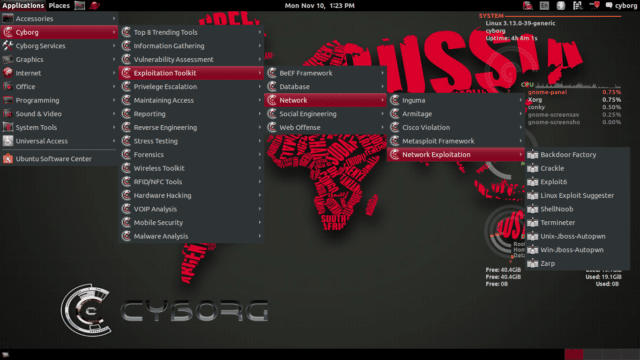
It’s clearly not as performant, advanced or polished as something like Kali – but it’s a good start and I hope the developers keep working on it and rope in some higher level security engineers to work on the OS optimization and driver stack.
Cyborg Hawk Linux Features
Cyborg Linux has quite an extensive set of modifications based on a Ubuntu subsystem with its own customised PPA repository.
The features are as follows:
- More than 750+ penetration testing tools included.
- Cyborg Hawk is totally Free and always will be.
- Can be used as live OS with full capability.
- Exploitation Toolkit, Stress Testing, Reverse Engineering, Forensics, Mobile Security & Wireless Security.
- Full virtual machine support in version v1.1.
- Now comes with its own repository.
- Reliable and stable.
- Various Wireless devices support.
- Well sorted menu, everything organised in a logical manner.
- The kernel is patched from injection.
Cyborg Hawk Linux Hacking Tool Categories
The 750 or so tools are grouped roughly in the menu in the following categories:
- Information Gathering
- Vulnerability Assessment
- Exploitation
- Privilege Escalation
- Maintaining Access
- Documentation & Reporting
- Reverse Engineering
- Stress Testing
- Forensics
- Wireless Security
- RFID/NFC
- Hardware Hacking
- VoIP Analysis
- Mobile Security
- Malware Analysis
Cyborg Hawk Download
You can download Cyborg Hawk Linux here:
Or read more here.
