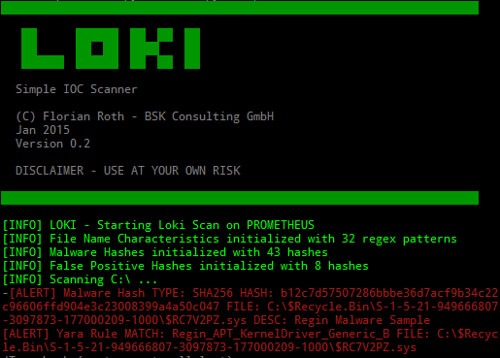
Loki is a Indicators Of Compromise Scanner, based on 4 main methods (additional checks are available) and will present a report showing GREEN, YELLOW or RED result lines.
The compiled scanner may be detected by antivirus engines. This is caused by the fact that the scanner is a compiled python script that implement some file system and process scanning features that are also used in compiled malware code.
If you don’t trust the compiled executable, please compile it yourself.
Detection
Detection is based on four detection methods:
- File Name IOC – Regex match on full file path/name
- Yara Rule Check – Yara signature match on file data and process memory
- Hash Check – Compares known malicious hashes (MD5, SHA1, SHA256)
- C2 Back Connect Check – Compares process connection endpoints with C2 IOCs
There are also some additional checks available:
- Regin filesystem check (via –reginfs)
- Process anomaly check
- SWF decompressed scan
- SAM dump check
Included IOCs
Loki currently includes the following IOCs:
- Equation Group Malware (Hashes, Yara Rules by Kaspersky and 10 custom rules generated by us)
- Carbanak APT – (Hashes, Filename IOCs – no service detection and Yara rules)
- Arid Viper APT – (Hashes)
- Anthem APT Deep Panda Signatures (not officialy confirmed)/li>
- Regin Malware (GCHQ / NSA / FiveEyes) (incl. Legspin and Hopscotch)
- Five Eyes QUERTY Malware
- Skeleton Key Malware (other state-sponsored Malware)
- WoolenGoldfish – (SHA1 hashes, Yara rules)
- OpCleaver (Iranian APT campaign)
- More than 180 hack tool Yara rules
- More than 600 web shell Yara rules
- Numerous suspicious file name regex signatures
Usage
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 |
usage: loki.exe [-h] [-p path] [-s kilobyte] [--printAll] [--noprocscan] [--nofilescan] [--noindicator] [--debug] Loki - Simple IOC Scanner optional arguments: -h, --help show this help message and exit -p path Path to scan -s kilobyte Maximum file site to check in KB (default 2000 KB) --printAll Print all files that are scanned --noprocscan Skip the process scan --nofilescan Skip the file scan --noindicator Do not show a progress indicator --debug Debug output |
The Windows binary is compiled with PyInstaller 2.1 and should run as x86 application on both x86 and x64 based systems.
You can download Loki here:
Or read more here.
