AddressSanitizer (aka ASan) is a very fast memory error detector for C/C++, Tthe average slowdown of the instrumented program is ~2x. The tool works on x86 Linux and Mac, and ARM Android. AddressSanitizer is based on compiler instrumentation and directly-mapped shadow memory.
The tool consists of a compiler instrumentation module (currently, an LLVM pass) and a run-time library which replaces the malloc function.
Features
It finds:
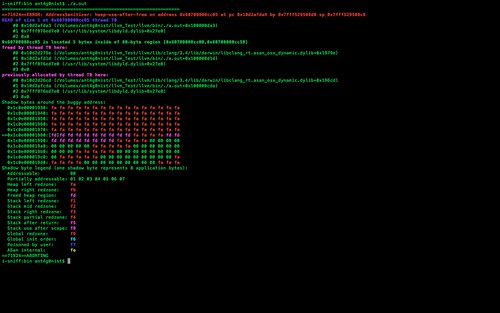
- Use after free (dangling pointer dereference)
- Heap buffer overflow
- Stack buffer overflow
- Global buffer overflow
- Use after return
- Initialization order bugs
Using AddressSanitize
In order to use AddressSanitizer you will need to compile and link your program using clang with the -fsanitize=address switch. To get a reasonable performance add -O1 or higher, and to get nicer stack traces in error messages add -fno-omit-frame-pointer.
Limitations
AddressSanitizer does not prevent any uninitialized memory reads, and only prevents some use-after-return bugs. It is also not capable of preventing all arbitrary memory corruption bugs. Arbitrary write bugs due to integer underflow/overflows (when the integer with undefined behaviour is used to calculate memory address offsets). Adjacent buffers in structs and classes are not protected from overflow, in part to prevent breaking backwards compatibility
You can get AddressSanitizer as a part of LLVM starting with version 3.1 and a part of GCC starting with version 4.8.
Or read more here.
