BlueScan is a BASH script that acts as a Bluetooth device scanner. It’s a tool designed to detect Bluetooth devices within the radio range of your system and extract as much information as possible from the devices without the requirement to pair.
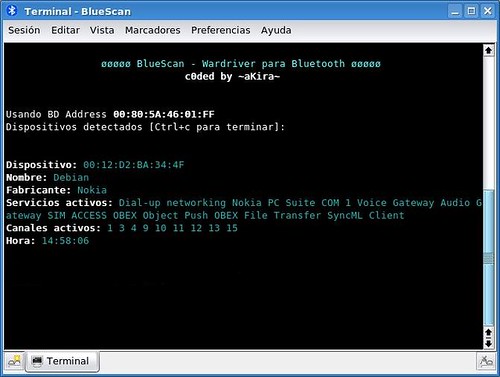
The tool works unobtrusively, ie without establishing a connection to the devices found and undetected. No superuser privileges are required to run it.
Requirements
- A GNU / Linux operating system
- A kernel version 2.4.6 or higher with the Bluetooth protocol stack implemented
- A Bluetooth adapter that provides the system with HCI interface
- Libraries – libbluetooth2 & bluez-utils
Features
Currently it is able to detect:
- BD device address (is equivalent to the MAC of a network card)
- Device Name
- Manufacturer (in most cases)
- Active services on the device
- Open channels on the device
One caveat, it’s in Spanish, so yah – you’ll have to figure that out.
You can download BlueScan here:
Or read more here.
