InsomniaShell is a tool for use during penetration tests, when you have ability to upload or create an arbitrary .aspx page. This .aspx page is an example of using native calls through pinvoke to provide either an ASP.NET reverse shell or a bind shell.
ASP.NET is an open source server-side Web application framework designed for Web development to produce dynamic Web pages. It was developed by Microsoft to allow programmers to build dynamic web sites, web applications and web services.
It was first released in January 2002 with version 1.0 of the .NET Framework, and is the successor to Microsoft’s Active Server Pages (ASP) technology. ASP.NET is built on the Common Language Runtime (CLR), allowing programmers to write ASP.NET code using any supported .NET language.
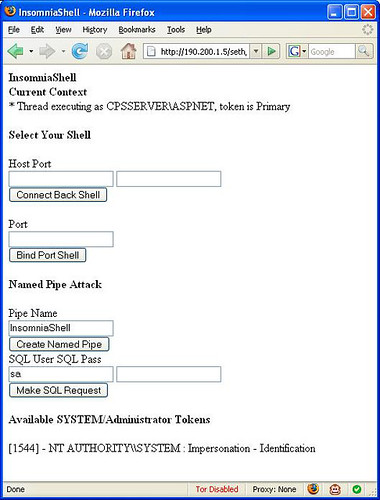
A bind shell is basically binding the command prompt to a listening port on the compromised machine, a reverse shell is sending a command prompt to a listening port on the attackers machine (used when the hacked server doesn’t have a public IP).
InsomniaShell has the added advantage of searching through all accessible processes looking for a SYSTEM or Administrator token to use for impersonation.
If the provider page is running on a server with a local SQL Server instance, the shell includes functionality for a named pipe impersonation attack. This requires knowledge of the sa password, and results in the theft of the token that the SQL server is executing under.
You can download InsomniaShell here:
